first level title
Why Web3 Needs Privacy Computing
Privacy is always the basis for protecting user rights and expanding the encryption market, and is one of the important directions of Web3. In the era of open and user-led Web3, privacy protection will be a standard configuration. From our daily life, we have all experienced the careful protection of secrets, such as a diary to record our mood, a tree hole to share secrets without revealing our identity, they represent our demands for active protection of privacy. With the increase in the demand for interactive activities, we need to passively provide some of our key information, out of the control of our own external protection, it is particularly important to prevent private information from being spread and doing evil. But the reality is that with the emergence of more and more analysis tools and the control of user information by centralized platforms, the problem of privacy information leakage has become more and more serious. Internet giants like Facebook are also The issue of leaks has been repeatedly named.
first level title
Privacy Computation Type
Specifically, privacy computing includes multi-party secure computing (MPC), zero-knowledge proof, trusted execution environment (TEE), etc. Below we briefly explain several privacy computing names to help everyone understand.
The Trusted Execution Environment is a secure area within the CPU, an independent environment built by means of software and hardware, and can run in parallel with an external operating system, that is, trusted applications running in this environment It can access all the functions of the internal CPU and memory, and hardware isolation can simultaneously protect the privacy and safe operation of internal and external programs. The trusted execution environment is still based on trusted hardware, just like a black box embedded, and the operator can use it invisible . Here we can use the analogy of the imperial palace in historical dramas that we are familiar with. As the emperor of the emperor, it will be well protected in an area. It is to protect the safety of the emperor. In terms of external communication, through intermediary transmission, internal and external information can be processed and understood simultaneously, which is the construction of a trusted execution environment. Of course, there will still be assassination moments, so in order to improve the safety factor, the trusted execution environment will adopt multi-party security technology for upgrade protection.
Secure Muti-Party Computation (Secure Muti-Party Computation) is a category of cryptography applications. It was proposed by Turing Award winner Professor Yao Qizhi in the Secure Computing Protocol published in 1982. A workaround for the authentication problem. This requires the joint participation of multiple participants, decentralization, and the premise of ensuring the security of information or data from multiple parties. For example, if we want to get a priceless treasure from a safe, opening the safe requires the cooperation of multiple people present or in custody to take it out, and the solution of this cooperation is different every time, people cannot tamper with it, and cannot disclose it in advance . This completely guarantees password security. Of course, multi-party security technology involves many parties, requires correspondingly more additional technologies, and requires more tests in technology upgrades and security guarantees.
Zero-Knowledge Proof (Zero-Knowledge Proof) is also a branch of cryptography applications. The more general explanation is that the prover can convince the verifier that a certain assertion is correct without providing any useful information to the verifier. It is this process that is credible, but the verifier has no way of knowing the real password except that the result is correct. We can understand it from the magicians magic. As the audience, we accept the magic result, that is, believe in the change result, but we still cant figure out how it works and cant solve the answer. This magical encryption process is the magic of zero-knowledge proof. Nowadays, many blockchain projects are using zero-knowledge proof as a privacy calculation method. Proof of knowledge technology enables encryption projects to protect the privacy of contributors addresses when issuing airdrops to active contributors.
image description
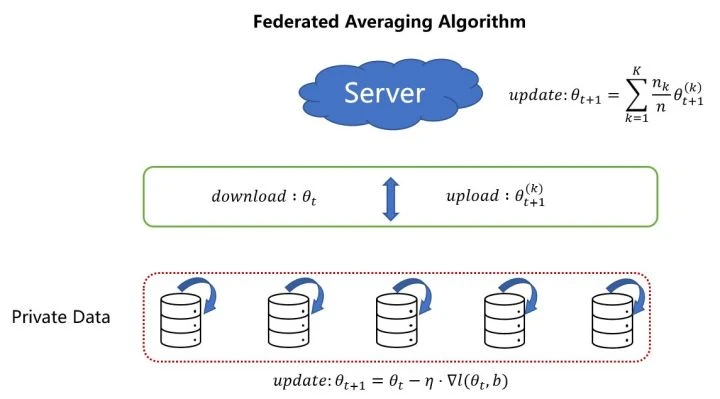
first level title
Privacy Track Project
image description

(picture source network)
Founded in 2018, Oasis has been committed to building a blockchain network with high performance, security and user privacy protection. The network is designed with unique and confidential ParaTime and supports confidential execution of smart contracts. Specifically in ParaTime, Oasis uses the trusted execution environment (TEE), a secure computing technology, to act as a black box for smart contract execution in confidential Paratime. The encrypted data goes into the black box along with the smart contract, the data is decrypted, processed by the smart contract, and then encrypted before being sent into the TEE to guarantee that the data remains confidential at all times. At present, Oasis is continuously supporting computing technologies such as multi-party secure computing and joint learning, and constantly strengthening the application value of the private computing public chain.
Iron Fish is a cryptocurrency transaction service provider. The goal is to protect the privacy of all transaction information, mining information, and wallet information, so that no second party can view it. The core privacy computing technology adopted by the project is the zero-knowledge proof zk-SNARK Groth16 Sapling proof. In order to achieve the goal of encrypting the general privacy layer, Iron Fish plans to support WebRTC and WebSockets at the network layer, which means that users can Run a full Iron Fish node directly. The latest news from Iron Fish’s ecological construction. The first incentive test network has officially ended, attracting more than 9,000 contributors to participate. Next, we will announce and start the second phase of the incentive test network for stress testing the main network and other preparations .
image description
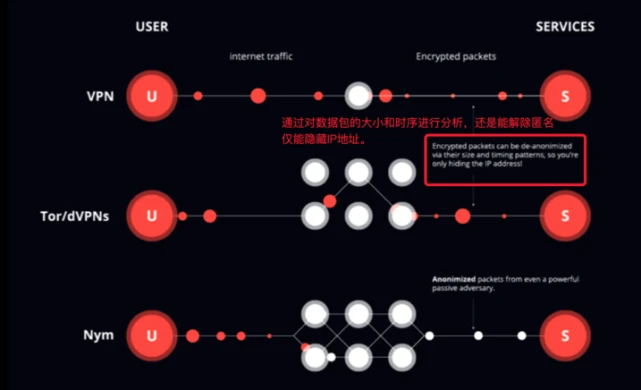
(Nym privacy protection process picture source network)
In addition to the construction of public chain infrastructure, privacy computing technology has also landed in anonymous coins, data privacy, private transaction networks and other sectors. Of course, most privacy infrastructure and applications are still under development and construction. As for when privacy technology will meet breakthroughs The next mile of development can only be answered by time.










