background overview
first level titlebackground overview
The Slope wallet team invited the SlowMist security team to analyze and follow up. After continuous follow-up and analysis, the data provided by the Solana foundation shows that nearly 60% of stolen users use Phantom wallets, about 30% of addresses use Slope wallets, and the rest use Trust Wallet, etc., and iOS and Android versions of the application have corresponding victims, so we began to focus on analyzing the possible risk points of the wallet application.
Analysis process
first level title
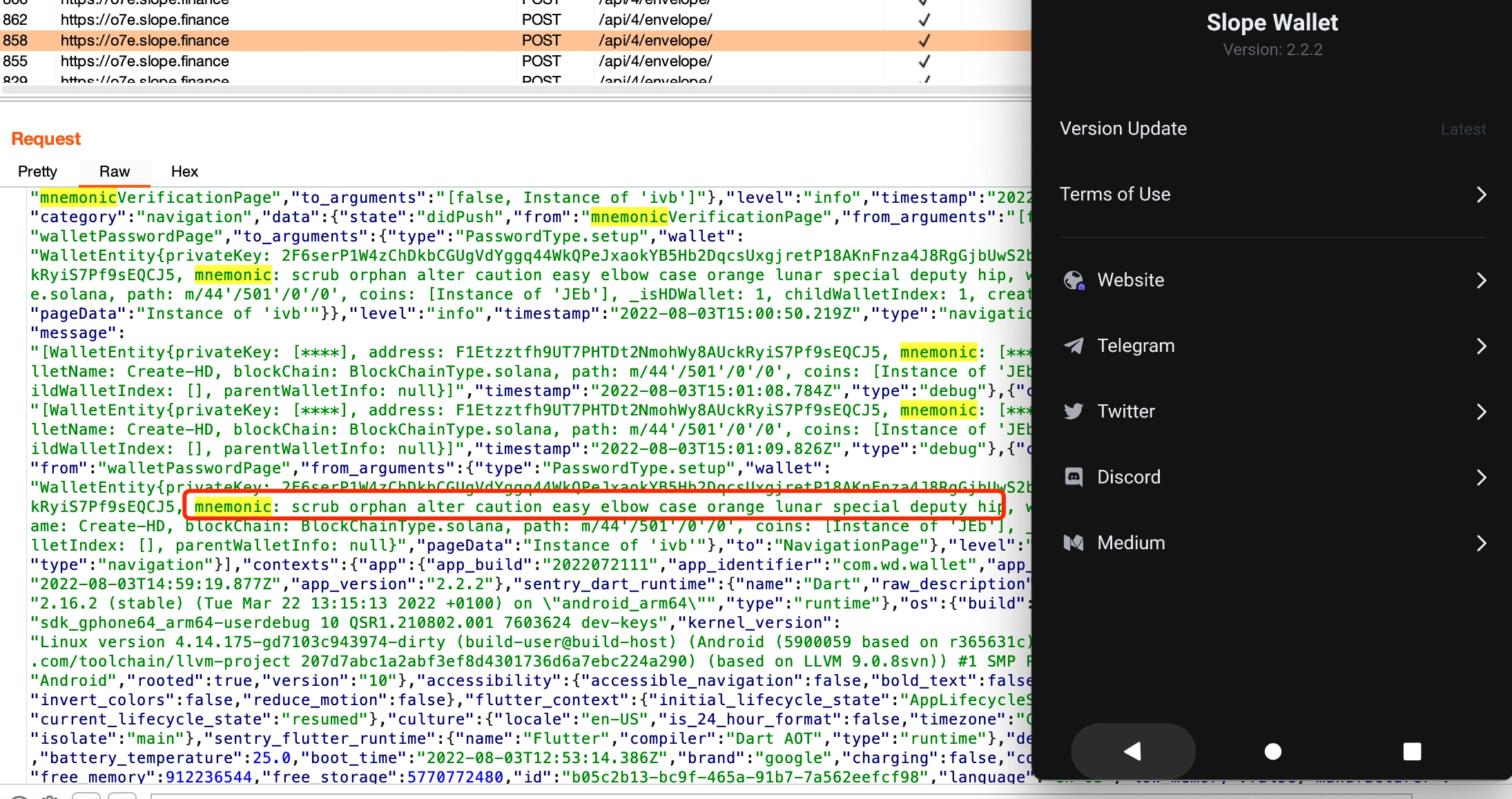
Analysis process"o7e.slope.finance"When analyzing Slope Wallet (Android, Version: 2.2.2), it is found that Slope Wallet (Android, Version: 2.2.2) uses the service of Sentry. Sentry is a widely used service, and Sentry runs on o7e.slope. Under the finance domain name, sensitive data such as mnemonics and private keys will be sent to https://o7e.slope.finance/api/4/envelope/ when creating a wallet.
Continuing to analyze the Slope Wallet, we found that the Sentry service in the Version: >=2.2.0 package will send the mnemonic to
https://apkpure.com/cn/slope-wallet/com.wd.wallet/versions
Slope Wallet(Android, >, while Version: 2.1.3 did not find the behavior of collecting mnemonic words.
Slope Wallet historical version download:
= Version: 2.2.0) was released on and after 2022.06.24, so users who use Slope Wallet (Android, >= Version: 2.2.0) after 2022.06.24 are affected, but according to some victims Feedback is not aware of Slope Wallet and has not used Slope Wallet.
After analyzing the Phantom (Version: 22.07.11_65) wallet, it was found that Phantom (Android, Version: 22.07.11_65) also used the Sentry service to collect user information, but no obvious behavior of collecting mnemonic words or private keys was found . (The security risk of the historical version of Phantom Wallet is still being analyzed by the SlowMist security team)
some doubts
The SlowMist security team is still collecting more information to analyze the reasons why the other 60% of stolen users were hacked. If you have any ideas, welcome to discuss them together, hoping to contribute to the Solana ecology together. Here are some points of doubt during the analysis:
1. Is Sentry’s service collecting mnemonic phrases from users’ wallets a common security issue?
2. Phantom uses Sentry, so will the Phantom wallet be affected?
1. Is Sentry’s service collecting mnemonic phrases from users’ wallets a common security issue?
3. What is the reason for the other 60% of stolen users to be hacked?
first level title
secondary title
Htp9MGP8Tig923ZFY7Qf2zzbMUmYneFRAhSp7vSg4wxV
CEzN7mqP9xoxn2HdyW6fjEJ73t7qaX9Rp2zyS6hb3iEu
5WwBYgQG6BdErM2nNNyUmQXfcUnB68b6kesxBywh1J3n
GeEccGJ9BEzVbVor1njkBCCiqXJbXVeDHaXDCrBDbmuy
secondary title
https://dune.com/awesome/solana-hack
Victims address:
https://www.odaily.news/newsflash/294440
https://solanafoundation.typeform.com/to/Rxm8STIT?typeform-source=t.co
secondary title










