TL; DR
1. SBT is a relational proof rather than an authoritative proof. Its value lies in the accumulation of a large amount of data. Complexity, richness and diversity will be the core competitiveness of SBT data sources.
2. The accumulation of data will endow each account with a soul. By preprocessing and classifying information, labeling and personalizing accounts can greatly enrich the application scenarios of identities on the chain, and even predict their behavior.
3. Privacy is a luxury, and editable privacy is a track with great demand but full of challenges.
4. The formation of a decentralized society requires strong binding between natural persons and identities on the chain, which increases the replacement cost of identities and creates identity dependence.
text
Table of contents:
text
text
text
text
text
image description
first level title
Decentralized society and soul-bound tokens
Vitalik once again mentioned POAP and its future possibilities at ETHCC in 2022. He said that POAP will be a way to distinguish real users from bot in web 3.0. This is not the first time that Vitalik has mentioned the POAP project. This earliest badge certification project has gained Vitaliks attention since its launch. As of 2022/8/1, there are already 916,332 wallets holding related badges, many Large-scale activities will choose to join the concept of participate to mint. Distinguish between real people and machines means that the identity and data of Web3 are no longer limited to the illusory world on the Internet, but break the boundary between virtual and reality, endowed with personality, and begin to compare with reality. In the Web2 Internet world established over the past few decades, characters are virtual, images are fictitious, souls are separated from characters and images, and reality and virtuality are completely separated. andIn the construction of Web3, the characters are real, the image is multi-faceted, and the soul is bound together with the real characters.image description
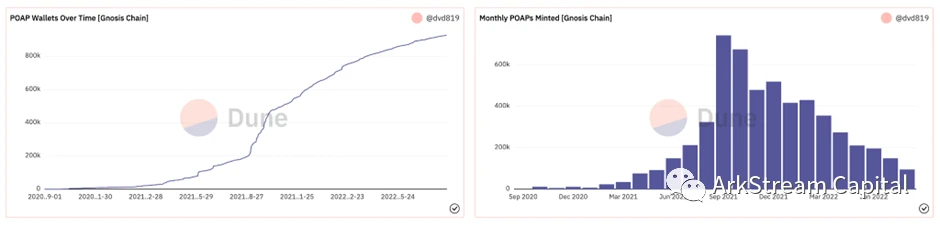
Figure 2 The number of wallets with POAP and the number of mint
The interpretation of the concept of soul binding in Web3 comes from Vitaliks description in the article Decentralized Society: Finding Web3s Soul, and the name comes from World of Warcraft. The article describes a Web3 society in detail. Compared with its description, our current market is like a train. It is not so Web3, at best it is Web2.5, from Tornado Cash supervision to DAO voting liquidation of whales. We have deviated from the original goal of the blockchain. This train is loaded with DeFi, GameFi, NFT and the concept of the return of various ownerships. The high degree of financialization and strong wealth creation effect attracts countless people who chase the train. In the long run, we may experience endless hacker attacks, witch attacks and Under the temptation of money, they gradually lost their faith in the industry and became blindly chasing profits. Especially in a crypto world where asset mobility is strong and punishment methods are lacking, chasing more benefits may become the only pursuit of Web3 residents. Pure financialization will not be conducive to the sustainable development of the entire industry. Whats worse, new technologies will cause wealth to be reshuffled again. That is, after the industrial revolution, a centralized system wrapped in decentralized sugar will appear.
Vitalik chose to pave a new track for this car, adding the Soul Bond Token (SBT) solution, thus guiding the direction of the entire Web3, from Web2.5 to a real Decentralzied Society, DeSoc, decentralized society. A truly decentralized society, DeSoc, has strong social composability. The social construction model is no longer a top-down model that is uniformly deployed by the centralized government, but chooses to return ownership and take the individual as the basis. The center spreads out to form a bottom-up people-oriented social system. In this social system, wealth is no longer concentrated,image description
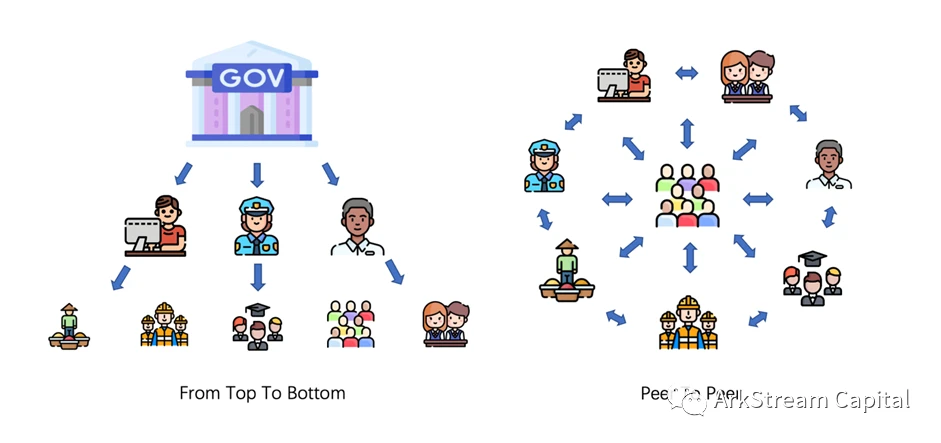
Figure 3 Top-down and bottom-up social systems
Vitalik believes that to achieve such a society,A publicly visible, non-transferable and wallet-bound token - the soul-bound token SBT is an essential part that will give each account humanity, thus making a decentralized identity increasingly full. SBT is similar to the previously mentioned POAP badge concept, but with the added non-transferable feature.It is a proof of relationship rather than a proof of authority.Lets use an example to illustrate what relationship proof is: Alice participated in Bobs birthday party and got a SBT. This SBT can only be used as a proof of Alices participation, but not to prove that Alice is Bobs friend. Their relationship can be positive or negative, close or distant. As Alice continues to participate in activities where Bob appears, a large amount of data accumulation can conclude that they are friends or even lovers. Now, if we replace Alice with an account, and Bob with DeFi and GameFi, we can figure out whether the identity behind a certain account is a game expert or a senior leek.
first level title
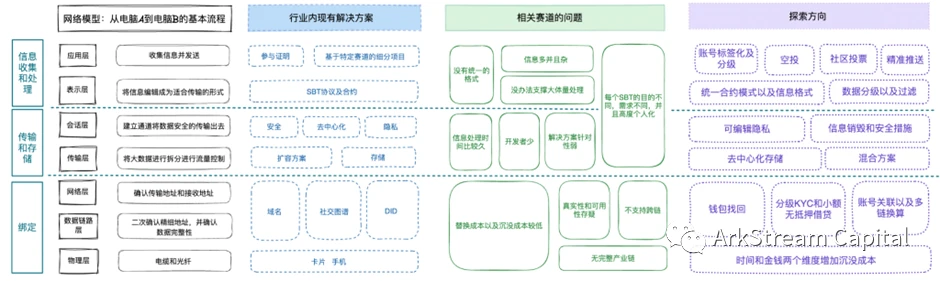
SBT and related track analysis under the OSI model
image description
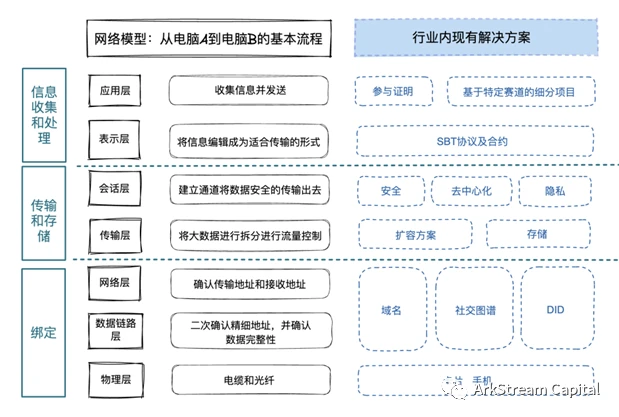
Figure 4 Industry classification under the OSI model
image description
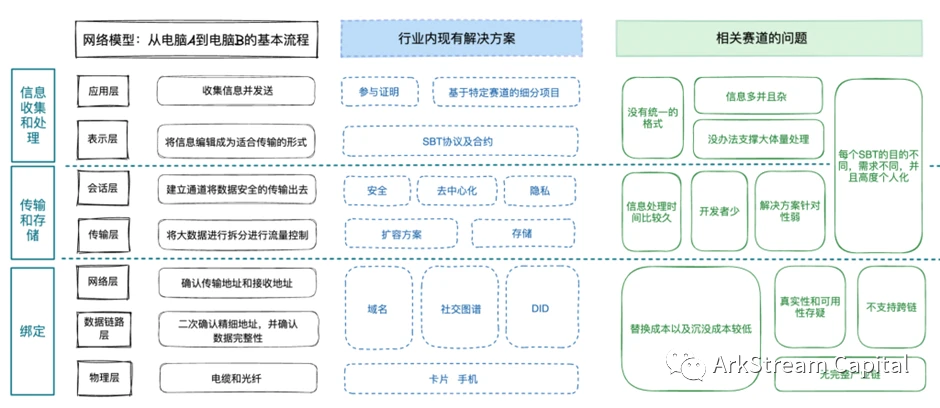
Figure 5 Industry classification and problems under the OSI model
Next, this article will cover the specific solutions at each level, take the existing SBT-related projects as examples, analyze the entire encryption industry ecology, and raise some common issues in the industry to discuss future exploration directions.
Information Collection and Processing
The collection and processing of information covers two levels: the application layer collects and sends information, and the presentation layer edits the information into a form suitable for transmission. These two levels are the most focused areas of SBT-related project development.The greatest value of SBT lies in the accumulation of a large amount of data, especially the data that cannot be quantified originally. These data will greatly improve the analysis of the behavior pattern of an account.image description
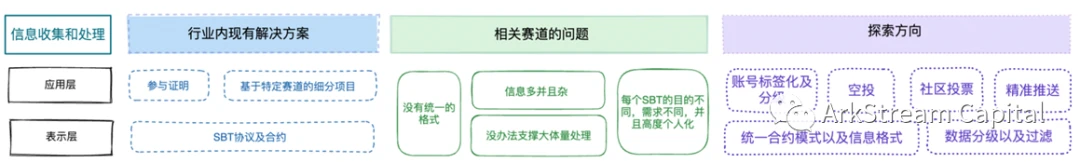
Figure 6 Information collection and processing
A. Application layer
At present, the development of the application side is mainly focused on two parts: proof of participation and subdivision projects based on specific use cases. Projects in this category aim to record relationships: some focus on the recording of individual actions, others on the recording of individuals and events. A lot of development is currently concentrated in this branch. The first category of common projects is to issue SBT to users based on the wallets existing behavior and transactions.
POAP
Although the earliest badge project is not SBT, as an initial related project, it can support the project party to hold activities and use the POAP platform to sell its own NFT, which can be transferred.
Quest3
A platform that provides various tasks for DeFi, DAO, and GameFi platforms. Users can participate in the community and reward SBT by completing tasks.
Noox
Based on the wallet address analysis and set up the corresponding SBT collection node. After achieving a certain achievement, such as using a certain DApp for a certain number of times, you can receive a SBT on the platform.
Project Galaxy
It aims to build a data certificate network, issue on-chain certificates to users on-chain and off-chain behaviors, and help developers use data certificates to calculate user credit points, find target audiences, and reward community contributors.
The second category is projects developed based on specific usage scenarios, such as DeQuest and CarvIO. At present, these scenarios are mostly concentrated in GameFi or DeFi, such subdivided tracks with a large user base.
DeQuest
Obtain SBT by learning about Crypto and games, and the game data can also prove your game level, and finally relevant data can become the basis for participating in the white list.
Carv IO
Reputation is formed based on wallet data. Now it supports viewing the status of multiple chain games, and after completing certain tasks, badges in the form of SBT will be issued. For game guilds, scholars can be selected and trained based on platform user data.
From the above projects, we can see that the current form of data collection on the application side is very single. The starting point of many projects is to try to analyze existing user behaviors, lacking multi-dimensional data in different scenarios, such as offline meetings, or using platforms data such as duration.We believe that complexity, richness and diversity will be the core competitiveness of SBT data sources.
In addition, although data certificate projects such as POAP and Galaxy were born before the release of the SBT concept, most of their data certificates are tradable NFTs, but their product form and final vision are similar to SBT, and the possibility of switching to SBT in the later period cannot be ruled out. Further enhance the network effect of users.
B. Presentation layer
The presentation layer focuses on the development of contracts and protocols. These agreements try to establish the general rules of SBT, which can be applied to various DApp development.
Marry3
The Paired Soulbound Token protocol is proposed, which can make the scene of marriage appear in Web3, and two accounts can be bound and divorced through multi-signature.
In addition to the development of SBT contracts based on specific projects, there are also a large number of contract projects in the market. EIP-4973 Account-bound Tokens, EIP-6114 Soulbound Nadges, ERC721S Soulbond. These are all contract types based on ERC-721, and as shown on the application side, they are basically identification contract types.Identification contracts can be used to issue participation certificates or graduation certificates, but they are not supported for those that need to be accumulated by quantity and time, such as reputation.This is also the problem of SBT development in the current application layer and presentation layer:
(1) For some protocols that require time dimension, contribution dimension or simple quantity accumulation, almost no one has developed them. In fact, these data that rely on accumulation and time to bring quantitative and qualitative changes are the key to SBT.
(2) A large number of protocol developments use completely different contract formats, resulting in messy SBT data, and the collected data cannot be merged and accumulated, which eventually leads to the scattered data on the application side. In the long run, these scattered data cannot be recovered. It is good to record and analyze the behavior of an account.
(3) The existing scheme does not carry out detailed processing and subdivision of SBT data. SBT is a highly personal application mode, and a large amount of data will cause useful data and useless data to be mixed. Just like red beans mixed with mung beans, it is difficult to screen them in batches. Because of the high degree of liberalization of information collection, most of the information formats are not only irregular, but also require manual sorting and filtering.Detailed screening of profitable data is also an essential part of SBT.
For these existing problems, we believe that SBT-related projects can make the following improvements in information collection and processing:
1. Enrich the product structure of the application side
At present, the products on the application side basically focus on issuing certificates and marking others, and the data collected in a single mode is often single. Application-side products should support the collection of different categories and dimensions of information and collect relevant data in a targeted manner according to specific application scenarios. At present, new rules are formulated for the DAO communitys voting, airdrop, whitelist and other behaviors. This part of the development market has responded very quickly. I am very much looking forward to new governance methods and participation statistics in the increasingly depressed DAO track. SBT can completely change the model of the DAO community and truly reward deep participants.
DAOU
DAOU uses Soulbound Token and Social Oracle to convert members activity data in DAO (Discord activity and participation, forum QA, Github code contribution, DAO roles and connections) into verifiable data on the chain.
2. Enrich usage scenarios through account labeling and personalization
Since SBT can build identity credit on the chain, why notAnthropomorphize accounts, endow each account with personality characteristics through data accumulation and analysis, and then predict reactions in specific environments based on personality characteristics.For example, if Bobs tag is Game Master, then in some games with a high degree of difficulty, it can be predicted by machine learning that Bob will have a high probability of buying and becoming a high-level player of this game. If a similar application is combined with lending, it is possible to predict within what amount a particular account will be repaid. The gameplay of this part needs to be explored, but tagged and personalized behavior can promote users to establish emotional links with accounts. Data analysis platforms such as Nansen already have labels for addresses such as Smart Money, and such labels can help build identities on the chain. Labels can also be linked to each other to accurately predict account behavior. For example, Bob is Game Master and Option Lover. From the simple account label, it can be analyzed through the behavior pattern that Bob’s behavior in the price range is the risk taker’s stop loss point in the corresponding game NFT. The behavior of a single account can be classified and analyzed and predicted according to the label. The personalization and tagging of accounts not only attracts users, but also simplifies the development of the application side. Not only that, because of the highly personalized attributes of SBT, it can customize precise push, precise marketing and personal product design for individuals.
3. Incorporate time into the direction of protocol layer development, and create a more unified protocol and developer tools
The current protocol development does not cover the time variable. At the same time, the current protocol development is in a state of individual play, and there is no unified protocol. The next direction of exploration should be to create a protocol with strong universality and ease of use. At the same time, based on the protocol, more mature developer tools are also required. If a more unified protocol cannot emerge in the short term, then the protocol developed based on ERC-721 can consider the corresponding data conversion and comparison. For example, there is a relatively uniform conversion standard between TOEFL and IELTS. Even if the pursuit of precision is lacking, user portrait analysis can be carried out within a general range.
4. Preprocessing and grading information
A large amount of information and irregular data format will make the record processing of the entire SBT extremely difficult. The reason why financial data is the easiest to develop is because the format is fixed. However, the data format of SBT has strong uncertainty. There is no way to identify whether the data is useful in a large amount of data. A more unified screening rule can be formulated at the application layer to roughly divide the data according to the priority. Data with higher priority, such as transfers or data with a higher confidentiality level, is classified into one category. Make less important data such as attending an unimportant meeting a secondary priority. Divide some data that is not clear whether it is useful or not into undetermined. Data processing and transmission are carried out in a targeted manner according to the priority of the data. Rough classification and grading of front-end applications can greatly reduce the difficulty of data processing, and also allow developers to focus on security and privacy maintenance.
transmission and storage
In the collection and processing of information, the functions of the application layer and the presentation layer have already integrated multiple data. Safe and efficient transmission is very important. The purpose of the session layer is to establish a secure channel to transmit data. The purpose of the transport layer is to split a large amount of data for flow control.
image description
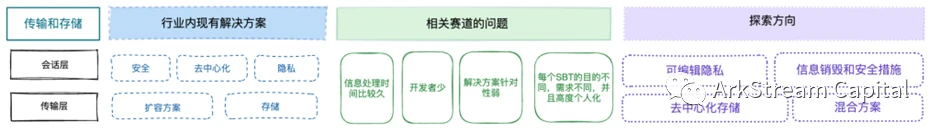
Figure 7 Transmission and storage
C. Session layer
The keyword for the session layer is security. This security includes not only the security of the wallet, but also the security of privacy and the pursuit of decentralization. SBT can provide creative solutions to security.
Burn My Wallet
A wallet security flagging software that notifies other users and protocols of hacked wallet addresses by minting SBT. These SBTs cannot be deleted and are bound to the account. Afterwards, as long as they access the API of the project party, they will receive a risk warning. Compared with existing centralized products that mark risk addresses, SBTs on-chain marking can help more people understand the security risks of wallets.
Such creative and new gameplay ideas will be a unique surprise brought to the market by SBT. Security programs currently on the market are all about telling the story of a stolen wallet locked or preventing it from being stolen. It is completely blank for the recovery of wallet property and the emergency measures for discovering stolen behavior. On-chain marking is a new gameplay brought by SBT. The exploration of this part may bring us a more complete security application software.
The technical characteristics of SBT make it difficult to achieve decentralization. Because the information and data of SBT are completely open source, even if the wallet is anonymous, as the binding of on-chain identity and off-chain identity becomes deeper and deeper, users pursuit of security, decentralization and privacy will become stronger and stronger .
From the users point of view, a series of pursuits such as privacy, security, and speed vary from person to person. These benefits should not be free, but should be categorized as services.Since everyone pursues a different degree of privacy openness, security level, and decentralization, these luxury goods should be clearly marked and classified.The degree of decentralization, level of openness and speed of each transmitted data comes from the price paid. Express delivery has special labels, fast labels, and the service should be fine. The pursuit of privacy should not be limited to encrypted transfers and identity hiding. At present, no matter whether it is a private public chain, a private transfer, or a highly decentralized or centralized public chain, there is no separate design for privacy.Editable privacy will be a new pursuit direction.
Privacy has three levels of classification: access, editing, and cashflow, that is, whether data can be accessed, edited, and used for profit. The three rights should be treated separately. The current privacy classification is simple and rough, either choose to hide completely, or choose open source hybrid, but the rough way cannot efficiently use the data generated by SBT.If privacy is classified in detail and charges are modularized based on different levels of development and maintenance, privacy projects will attract a lot of attention from the market. At present, the markets perception of privacy is still at the level of protection, but no one has focused on the profit of selling privacy and the fees for access. In the future, everyones privacy and openness will be determined by themselves, priced by themselves, and maintained at their own expense. Consumption privacy will become the mainstream in the future. Only by endowing privacy with a certain degree of profitability can the public who dont pay much attention to privacy take up arms and defend privacy.
D. Transport layer
The existing solution of the transport layer is how to process a large amount of data. The behavior of processing a large amount of data can be understood as whether it can be uploaded in large quantities, whether it supports data storage, whether it can identify the data on the chain and the data that needs to be stored. The solution at this level, put in the entire cryptocurrency industry, is the problem of expansion and decentralized storage that everyone is discussing. The problem corresponding to SBT is relatively simple but obvious: how to identify a large amount of redundant data and how to choose storage. Way. These questions have no standard and are completely personal. Even though the data preprocessing mentioned above, in fact, the collected data of the fully spread application layer cannot be processed at the same time.
Storage is the biggest challenge facing the SBT track. How can so much data be stored so that it can be retrieved arbitrarily and not lost under the condition of ensuring authenticity? Decentralized storage requires a lot of manpower and material resources to maintain, and its efficiency is very slow, but centralized storage is not trusted by the market. Based on this situation,Farcaster adopts a semi-centralized storage solution-hybrid storage, which may be a compromised solution for the current situation.Since the information classification is mentioned above, is it possible to save the highest level of information on the chain, but save the remaining unimportant data off the chain, or entrust a unified storage service, similar to AWS. Perhaps combining the two, benchmarking the priority and the degree of decentralization with each other, and choosing the optimal solution in this is the effective way out.
The problem of transmission and storage is not only a problem faced by SBT, but also a common problem in the crypto industry. We believe that the following development directions can bring new thinking to Infrastructure while accelerating the development of SBT.
1. Benefit customization and tiered fees
People with high needs for privacy, decentralization, and security can choose to pay high maintenance fees. Those who are relatively weak in pursuit of privacy and decentralization will choose a rougher solution. By grading the rights and interests and charging fees, the income generated by this part can be used to reward maintenance personnel, so as to ensure the corresponding enthusiasm.
2. Editable privacy
Even if it is privacy, a single pursuit cannot satisfy the increasingly complex user population. In the future, customization will be the most common feature. With the process of globalization, the integration of communities and the popularity of personalization will greatly affect our behavior patterns. Privacy will be the bellwether of the next era. Editable privacy will be another fusion of rights and technology.
3. Hybrid Storage
Inefficient and expensive decentralized storage will face great challenges, and the mature centralized model cannot be replaced in the short term. The confrontation between the two models will produce two situations: either decentralized storage can be efficient and store and transmit a large amount of data, or the entire industry chooses to compromise and choose hybrid storage until the singularity of technology appears.
to bind
Binding is a point that is repeatedly questioned in all concepts of SBT. Most people think that even though SBT can record all behaviors and allow us to have a second identity on the chain as an individual, if the wallet account can be changed at will, it means that the binding is in vain.We believe that the formation of a decentralized society requires strong binding between natural persons and identities on the chain, resulting in identity dependence.
Compared with reducing the cost of identity switching, increasing the cost is beneficial to the construction of Web3. If the cost of replacement is greater than the benefits after replacement, then most people will choose to maintain the current state, thus achieving binding. In addition, human nature is lazy, and long-term behavior habits will once again increase the cost of replacement. Correspondingly, the cost that can affect users has two parts: 1. Time 2. Money. Increased replacement costs can constrain humanity in the absence of punitive means. SBT has its own time cost, which can force users to spend a lot of time on an account under the accumulation of a large number of long-term behaviors, and users will be rewarded for their long-term efforts. On the contrary, the cost of money will be greatly weakened because of the transferability of crypto assets, which is a problem that needs to be solved.
In addition, it should be noted that increasing the replacement cost of identity is beneficial to binding, but it is by no means increasing the replacement cost of account address, which will bring more serious problems.image description
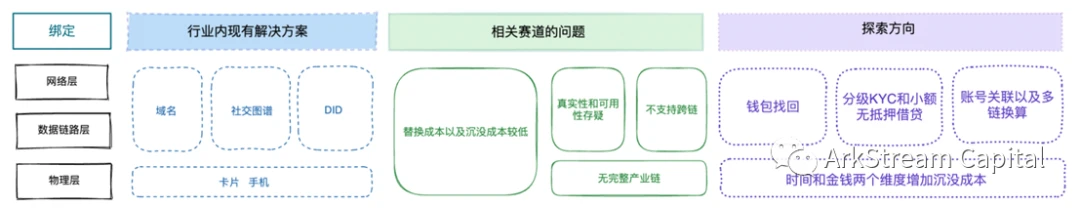
Figure 8 Binding
E. Network layer and data link layer
The most important role of the network layer and data link layer in the Internet is to confirm the transmission address and receiving address. The representative in Web2 is the IP address. In Web3, the wallet public key and private key system can best reflect the binding and receiving address. . The current market solutions focus on improving the ease of use of user portals. Irregular hash functions such as public keys and private keys greatly reduce the ease of use of wallets, just like complicated mailboxes and bank accounts that provide nickname functions. The domain name project headed by ENS tries to increase the ease of use of the wallet and reduce the difficulty of use.Increased ease of use will make wallet binding easier and easier to identify.
But users can do nothing about wallet replacement and discarding caused by forgetting, theft, and other security risks. The loss and theft of the private key will cause the identity to be no longer trusted, so how to retrieve the wallet is particularly important.SBT can achieve real wallet recovery. If the authenticity of the relevant holder can be confirmed through SBT, then it is also possible to determine whether the person really exists through the contribution of an account in the community and the connection established with community members. Vitalik wrote in Desoc that if users lose their private keys, they can regain ownership of their wallets through the community. The easiest example to understand is WeChat account recovery. Relatives and friends can help users retrieve their account by sending specific messages to WeChat. SBT will endow the encrypted world with the same relationship and authenticity. This direction of exploration can add new possibilities to existing wallet security.
A large number of wallet or user portal related projects focus on how to popularize wallets and increase the ease of use of wallets. For example, Metamask has gradually added NFT display from the initial token display, and embedded its own swap system.
Torus
It can help users generate and manage their own private keys, and can also authorize accounts to be managed by others.
Wallet security and ease of use are double-edged swords. The threshold for using wallets cannot prevent users from discarding their identities at will, and most users actively hold multiple wallets and change them at will. The most fundamental concept of binding is whether it is possible to bind a natural person with the identity on the chain represented by the wallet.In other words, there is a real person behind the on-chain behavior and that person is not generating wallets in large numbers for profit. The two most common item categories are social graphs and DIDs. Social graph protocols led by Lens Protocol and Cyberconnect try to integrate all behaviors on the chain, and data can be shared in the same system, so as to achieve the unity of identity on the chain. Now many new social graph projects are trying to combine SBT and social graph.
Flamingle Labs
Flamingle Labs is a Web3 social product based on offline activities. Users can naturally socialize with Web3, thus building a distributed social account map. The project hopes to solve the problems of too few valid Web3 social users, full of false accounts, and too flat user DID by transforming offline activities.
The track that keeps pace with the social graph is DID. DID can be said to be the most successful track bundled with SBT. DID projects either focus on discovering account attributes through the analysis of a single address, or associate off-chain data with on-chain.
DefNetwork
Def Network is a collaborative tool for creating user tags for wallet addresses. After downloading the plugin, Def Network can. Integrate and analyze the on-chain data of addresses, and generate labels. Developers and users can index specific tags and query addresses on Def Network.
IdentDeFi
Web3 identity information plug-in, the user connects to the wallet, links to the bank, and obtains KYC certification, so as to mint a non-tradable NFT to complete the identity certification. The project uses Zk-proof technology to ensure user privacy.
KNN3
Based on a set of behavior analysis logic, KNN3 screens and classifies the behaviors on the chain, takes the address as the unit, adds attributes to the address through behavior analysis, or establishes a relationship between two addresses, so as to understand the relationship between accounts and develop social interaction Atlas.
Whether it is a social graph or DID, if it can be combined with SBTs related technologies, it will be able to get twice the result with half the effort. The existing methods of binding off-chain identities and on-chain identities are too rough, and most of them will choose methods with low security, such as uploading documents and binding bank cards for KYC. In fact, not all identity verification requires off-chain KYC to complete, and SBT combined with on-chain behavior data can replace part of the use of KYC.We believe that KYC can be used in stages, and some low-security behaviors, such as airdrops, can be verified by SBT to screen out deep participants.Some behaviors that require high security, such as lending, require identity verification and auxiliary verification of SBT data. The essence of lending is a trust mechanism, how the borrower can ensure that the lender can repay the money through the trust mechanism. In traditional society, the behavior of borrowing money is highly bound to social relations. A persons reputation, social status, and economic strength can most affect a persons ability to borrow money. The characteristic of SBT is to bring a network of relationships into the chain. This network of relationships has costs. When the cost of giving up a wallet is greater than the amount of a small loan, this loan scenario that does not need to know the real identity of the other party is established.SBT can determine the amount of unsecured loans for small loans in different gears by building credit points on the chain, the longer the time, the deeper the participation in the community, and the account with a complex relationship network, the more money can be borrowed without collateral or with a low mortgage rate. Exploration in this direction can be dreamily linked with multiple tracks such as NFT and DeFi.
F. Physical layer
The physical layer is a special level. In Web3, apart from mining machines in various senses, it is difficult for us to find objects corresponding to fiber optics and cables. corners quietly spread.
NFTPlay
Taking the NFT picture frame as the starting point, create a DID exclusive NFT mobile display device, combine the DID identity corresponding to the NFT with the exclusive mobile hardware, and explore the interactive scene between digital identity and the real world.
From the NFT display display produced after a series of NFT products such as Artblock became popular, to the Android smartphone of Solana Mobile Stack--Saga, they are all sending us a new message: the fiber optics of Web3 have sprouted, and products that meet various application scenarios have started to appear. As proposed at the Hannover Messe in 2013, Industry 1.0 is the era of steam engines, Industry 2.0 is the era of electrification, Industry 3.0 is the era of information, and Industry 4.0 is the era of intelligence. A new industrial revolution that endows machines with intelligence, and loads invisible and intangible algorithms, computing power, and information flows into entities is taking place, and the barrier between reality and virtuality is at stake.
In the future, we may see some products that use Web3 identity binding as an application scenario. These products fully serve the identity on the chain and will be deeply bound to the real world. In addition to mobile phones, there may be new, unexpected items bound to people: chips, bracelets, and even crystal implants. These unimaginable products,Increase the cost of replacement, so as to ensure that the soul of the identity is deeply bound to it, making it difficult to replace.
To sum up, in the binding step, the network layer, data link layer, and physical layer that are more closely connected with the physical world are involved. When we expand SBT to the level of identity, wallets, social graphs, and physical devices are some directions that can be explored. We believe that only by increasing the cost of replacement, SBT can further deeply bind with people. Based on this assumption, we have summarized some industry problems that can be improved through SBT:
1. Wallet recovery
The high replacement cost binds people more closely to their identity, and with it comes the issue of wallet security. Through the social relationship established by SBT, the wallet can be retrieved or replaced under the condition of multi-person cross-validation.
2. Alternative off-chain KYC for credit lending
SBT, which combines the relationship on the chain, allows each identity to have a cost. When the loan amount is less than the cost, a loan model that does not need to verify the real identity of the other party is established. SBT can combine credit points on the chain to provide micro-loans in different gears, filling the gaps in those scenarios that require KYC identity information to be on-chain for lending.
3. Physical equipment and reality coexist
In the future, we will see some physical devices with Web3 identity binding as the application scenario, fully serving the identity on the chain, so that the soul of the identity is deeply bound to the individual.
The future direction of SBT
Compared with the bottom-up Web3 stack theory, we refer to the OSI model, from the users point of view, disassemble the users behavior, divide the behavior of soul binding into three steps, and then discuss the steps involved in each step. Industry issues and directions for exploration. Since Vitalik put forward the concept of SBT, Buidlers in the industry have explored in various directions. We used the topic of SBT to think about some existing problems in the decentralized society and Web3, and also made some suggestions for the future development direction of the industry. got the prediction:
1. Agreement is king
The first batch of SBT-related projects in the market will focus on establishing rules and unifying agreements. The blooming of the application layer will appear after the emergence of relatively unified protocol rules related to SBT.
2. Everything on the chain
There will be more and more offline behaviors and on-chain interactions to issue participation certificates in the form of SBT. These certificates do not need to be real or meaningful at the beginning, but only need to be enough. When the amount of data is large to a certain extent, effective screening and classification mechanisms can help to effectively establish identities on the chain
3. On-chain credit and DeFi composability
Even though the original intention of Vitalik to put forward the concept of SBT is to solve the current high degree of financialization of the Crypto industry, the financial application brought about by the generation of credit is indeed an area that is easier to be accepted by the market. DeFi is currently still limited by over-collateralized lending. If credit lending can be fully introduced, new vitality may explode.
4. Privacy editing and re-empowerment
image description

Figure 9 Application, data, and soul binding
In addition, the way of thinking based on user behavior is not only suitable for SBT, all re-applications and user-related tracks can be substituted into this model. The transmission and storage layer is like a huge water purifier. After the protocol is formatted, all the data collected by the application end enters this huge water purifier. Some content is stored on the chain, and some is passed After the water purifier is carefully filtered and processed, these data are diverted to different pools under the different needs of all parties. There are extremely personal data and information of each person in the small pool. These information and data can pass through the middle filtering layer and be used by application developers for different purposes again. Closed loop, endless life. Eventually we will find that,The common problems that the entire industry cannot do without are expansion, storage, security, privacy, and decentralization. Any major breakthrough in the underlying direction is enough to support the vigorous development of the application layerReferences:
References:
[1] https://dune.com/dvd819/poap-summary-dashboard
[2] https://zhuanlan.zhihu.com/p/347036222
[3] Decentralized Society: Finding Web3s Soul
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4105763
[4] https://mp.weixin.qq.com/s/fUxVx9HK8J44HOf6Y1yqKA
Original linkhttps://www.farcaster.xyz/docs/intro










