Original source: R3PO
The focus of the encryption world has experienced multiple changes in Bitcoin, Ethereum, DeFi, NFT, Metaverse and Web3, but there is a lack of attention to encryption technology itself, except for Bitcoins elliptic curve encryption algorithm (ECC). Public awareness, other encryption algorithms basically stay in the self-promotion of researchers and developers.
R3PO believes that this is not decentralized enough, which will seriously hinder the further expansion of Web3. Cryptography is the basic piece of blockchain, and should not be mastered by a few people, but should go to a broader field.
R3PO hopes to use a new writing paradigm to explain the meaning of terms, taking into account both professionalism and readability, and is committed to discovering potential development opportunities for institutional investors and project parties.Investment opportunities, entrepreneurial direction and entry point, find the unusedAlpha revenue from mining。
The recent hot zero-knowledge proof technology is still a segmented field that is constantly developing and innovating, but its technology itself has a wide enough application scenario, so it is very important to sort out its panorama.
Zero-Knowledge Proof technology (Zero-Knowledge Proof) is not a new concept. After a careful review, it has been developed for 40 years, and a variety of models and applications have been born.
Entering the era of Web3, as early as 2017, V God has noticed the potential of ZK technology in Ethereum, and recently Starkware received 100 million US dollars in financing, bringing its total financing amount to 225 million, which means that the organization is based on the public chain Look at ZK technology with its level of valuation and potential. This will be a field of long-term fierce competition, and more investment opportunities will be exposed.
Deducting 20 years backward, R3PO believes that the development of ZK has at least the life span of a Jiazi. Therefore, describing the entire development process of ZK needs to be traced back to the source to better clarify its development logic and find potential opportunities for the next step.
first level title
secondary title
1982: If the wealth is not disclosed, the high and low will be distinguished

The pursuit of wealth has existed since ancient times. Xiang Yu once said: Wealth does not return home, it is like a night walk in brocade, but too much wealth will attract people to covet. Is there a way to not reveal the amount of wealth at the same time? How to compare the amount of wealth?
In 1982, Yao Qizhi, the later winner of the Turing Award, conceived this problem. This is the famous millionaire problem. The mathematical process is omitted. The general operation mode is as follows:
Alice and Bob choose the numbers i and j that represent their own wealth, and the value range is between 1-10;
Alice performed on ione-way encryption, and send the encrypted result k to Bob, and Bob gets a new value related to i;
Bob will get a new value m after operating on k, and pass it back to Alice. At this time, Alice can judge the relationship between m and i.
This process can continue to be deduced, and the two parties can finally complete the comparison without completing the information disclosure.
Of course, the above process is not comprehensive, but it is enough to illustrate a problem. We can indeed perform calculations between two parties without revealing information. If we expand the two parties to multiple parties and expand the interval to a larger range, Then this is a typical MPC (Secure Multi-party Computation) problem.
The millionaire problem is a starting point for ZK discussions:
Under the premise of not revealing wealth information, it meets the definition of zero knowledge;
secondary title
1985: Zero-knowledge proofs are introduced

In 1985, Goldwasser, Micali and Rackoff proposed the Zero-Knowledge Proof model for the first time. To be precise, it is an interactive zero-knowledge proof model. size.
The zero-knowledge here is not completely accurate. Take the interaction between Alice and Bob as an example. Alice and Bob can be verifiers and certifiers for each other, but the information passed between the two cannot be related to the amount of wealth itself. The zero-knowledge here is Refers to zero correlation, not non-informative.
And interactive means that the interaction can be performed multiple times, and this process can be repeated until the correct result is obtained.
secondary title
1991: Non-interactive zero-knowledge proofs

When the time came to 1991, Manuel Blum, Alfredo Santis, Silvio Micali, and Giuseppe Persiano proposed non-interactive zero-knowledge proofs, which are well known. It may seem counter-intuitive to verify the truth or falsehood of a theorem or hypothesis while interacting, but there is a wonderful example to illustrate:
Alice and Bob turned into mathematicians after their wealth became free. Alice leaves web2 to travel around web3, during which Alice continues ZK research.
We assume that Alice can write a postcard to Bob when she discovers a proof of a new theorem, proving that she has made new progress in her research.
This is a non-interactive process, to be precise, it is a one-way interaction: only from Alice to Bob. Even if Bob wanted to answer, he couldnt. Because Alice doesnt have a stable (or predictable) address, shell move out before any mail can reach her.
We agree that as long as Bob receives the email, we dont need to check the content of the email to determine that the proposition Alice has made new research progress is true.
The non-interactive zero-knowledge proof reduces the number of interactions to at most one time, and can realize offline verification and public verification. The former lays the foundation for the validity of Rollups, and the latter couples the broadcast mechanism of the blockchain to avoid the problems caused by multiple calculations. Waste of resources.
So far, the ZK we have seen so far has become a mature theoretical model, but at this time ZK is more of a research object in the field of mathematics and cryptography, and has little connection with the blockchain. After the emergence of Bitcoin, encryption Technology + blockchain has become the direction of research, and ZK is undoubtedly the best among them.
first level title
secondary title

2010-2014 Zcash: SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) practical scenarios
After the emergence of the Bitcoin network, security and privacy became peoples initial perception of the blockchain. A series of privacy-based public chains and applications have appeared on the market, such as SNARKs used by Zerocash/Zcash, and Bulletproofs (BP) used in Monero.
In 2010, Groth realized the first ZK based on ECC algorithm, O(1) constant level. That is, ZK-SNARKs or ZK-SNARGs.
SNARGs: Succinct Non-Interactive Arguments
SNARKs: Succinct Non-Interactive Arguments of Knowledge
From the perspective of application, this improvement lies in the simple Succinct function. Specifically, SNARK is dedicated to compressing the size of the information itself. In ZCash, the program circuit is fixed, so the polynomial verification is also fixed, which makes setting It only needs to be executed once, and the subsequent transaction can be reused only by changing the input.
In 2013, the Pinocchio protocol improved the efficiency to minutes-level proof and millisecond-level verification time, and the overhead was controlled within 300 bytes. This is also the first time that ZK-SNARKs technology has truly landed in the blockchain field.
This proves that ZK technology can play a role in privacy scenarios. R3PO judges that the subsequent privacy route will have the potential to exist independently of L2. Aztec has proved the feasibility of the privacy DeFi route. After tornado is sanctioned, financial privacy on the chain remains the same. It is a strong rigid demand. Investment opportunities in this direction have not been widely explored, and it is worth looking forward to.
secondary title
Mina: recursive ZK compressed data
Mina is different from Ethereum L2. It is an L1-level high-performance public chain. Its operating node is only 22KB. The reason why it can be so small is that it uses recursion to prove the validity of ZK confirmation, that is, every Each message carries previous confirmation results.
Step1: zk-SNARKs proves the validity of the node, and only needs to save the proof result;
Step2: Through recursive calls, ensure the correct transmission and retrieval of node validity, do not need to keep all historical data, and achieve the effect of extremely compressed data;
Passing the validity of the result instead of saving the full node data is Minas effective means of proving, and in Ethereum L2, ZK-Rollup can complete the validity proof by packaging multiple transaction data and settling once, while Further deduction, L3 can be superimposed on top of L2, or Dapp applications. These are the subdivision tracks that ZK can develop. For example, dYdX currently runs on Starkex, and L2 ImmutableX, which is built on top of Starkware, proves the strength of ZK. The use potential, the value of this track has not yet been fully tapped, and there is still long-term investment value.
So far, all the technical elements involved in ZK-Rollup have been basically completed. We have equipped enough basic knowledge of ZK, and can summarize the following characteristics of ZK:
Non-interactive: multiple verifications are not required, and only one verification can be broadcasted to the entire network;
Zero-knowledge: No need to disclose the characteristics of the information itself, and it can be publicly disseminated throughout the network;
Knowledge: Knowledge is not public and easy-to-obtain information, it must have unique value, such as economic value, privacy value, etc.;
Proof: The proof is confirmed by mathematical means, and the safety has been tested by years of research and practice;
first level title
secondary title
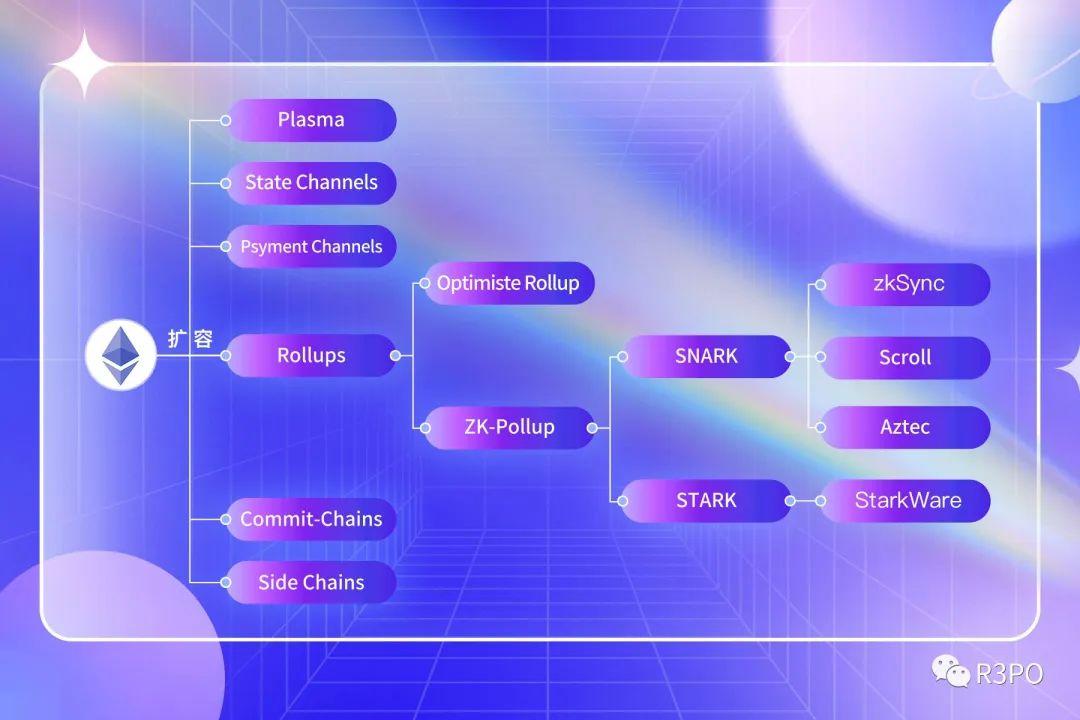
ZK-STARK: Seed player with 10-year development difficulty
Comparing the difference between the two, the main reason is that the S in STARK means Scalability, which is oriented to complex use scenarios of larger data, but it is still a technical route under development as a whole.
This article does not touch on the specific differences between L2, but one thing is obvious, except for StarkWare, other L2 projects, including zkSync, Aztec, Loopring, Scroll, etc., all adopt the SNARKs technology route.
The reason is that the development of STARK is too difficult. At present, only StarkWare has the ability to conduct self-development, but its benefits are also very obvious. Compared with SNARK, it can carry a larger amount of calculation. When running large data, Its security will be higher, such as games, social, NFT and other directions.
Secondly, the STARK route has the characteristics of anti-quantum attack, which has the possibility of overturning the industry structure in the next ten years. The ECC algorithm adopted by Bitcoin does not fully have the possibility of anti-quantum cracking. If zk-STARKs technology is added, its security will increase significantly.
secondary title
ZK-Rollup: Up-drilling of data, down-drilling of information
After the introduction of zk-STARKs, all the technical features of L2 expansion are complete, only the introduction of Rollup is missing. In fact, Rollup uses ZK’s verification mechanism to get rid of its demand for data volume: in L1, it is responsible for consensus and Under the premise of settlement, L2 is responsible for the specific daily operation of the application. Users do not need to interact directly with L1, and their experience will be highly similar to the current App.
Summarize
Summarize
We started from the millionaire problem and transitioned from the MPC problem to the field of zero-knowledge proofs. For economic reasons, interactive zero-knowledge proofs are not fully suitable for on-chain activities, and non-interactive zero-knowledge proofs have gradually become mainstream.
With the development of Zcash, SNARKs technology is increasingly applied to it, making ZK technology transform from a pure cryptography research object to an engineering method used in the blockchain field, and play its role in privacy, security, and efficiency.
The Ethereum expansion scenario has enabled ZK to achieve L2, the Rollup technology route has defeated other competitors, and zk-STARKs have gradually developed, which is expected to activate more common usage scenarios such as mining, GameFi, and NFT.
Outside of Ethereum, more and more new models have gradually emerged, such as the customizable and modular Rollup route, and Eclipse, which has just completed financing of 15 million US dollars. Scroll, which raised USD 10,000, hopes to build an EVM-equivalent ZK-Rollup.
Original link










