Original Author: Lisa Kong
Recently, we found many phishing incidents about eth_sign signatures.
Phishing website 1: https://moonbirds-exclusive.com/

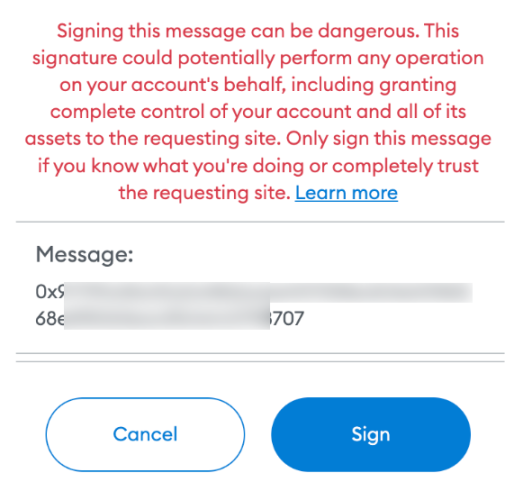
When we connected the wallet and clicked Claim, a signature application box popped up, and MetaMask displayed a red warning at the same time, and it was impossible to tell from this pop-up window what the signature was required for.
In fact, this is a very dangerous type of signature, basically Ethereums blank check. With this phishing, scammers can use your private key to sign any transaction.
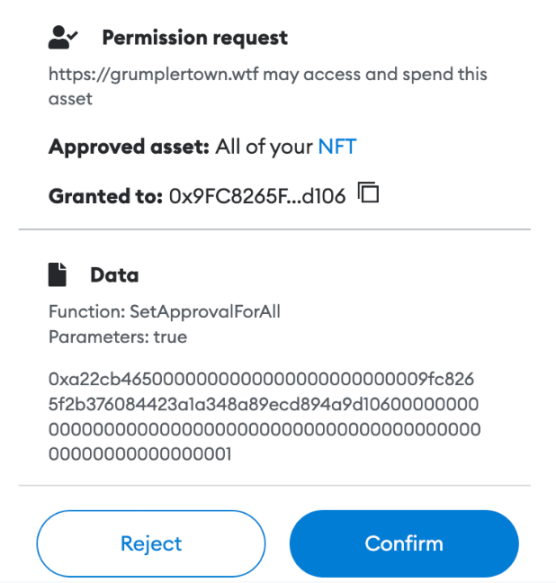
In addition, there is another kind of phishing: after you reject the above sign, it will automatically display another signature box in your MetaMask, and cheat your signature while you are not paying attention. And look at the signature content, the SetApprovalForAll method is used, and the target of Approved asset is displayed as All of your NFT, that is to say, once you sign, scammers can steal all your NFTs without restraint. as follows:
Phishing site 2: https://dooooodles.org/
We use MistTrack to analyze the scam address:
0xa594f48e80ffc8240f2f28d375fe4ca5379babc7
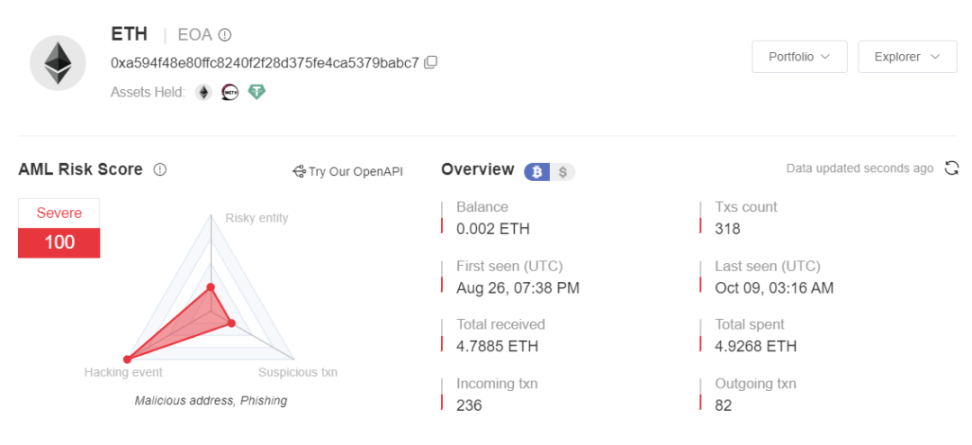
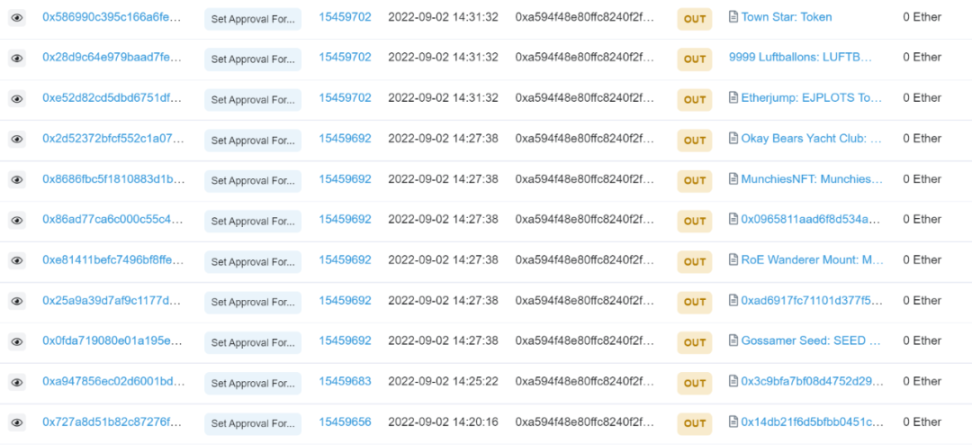
Through analysis, the scammer called SetApprovalForAll multiple times to steal user assets. The scammers address has received 33 NFTs, and after selling some of them, he got over 4 ETH.
Back to the topic, lets study this fishing method. First, lets see how MetaMask officially explains:
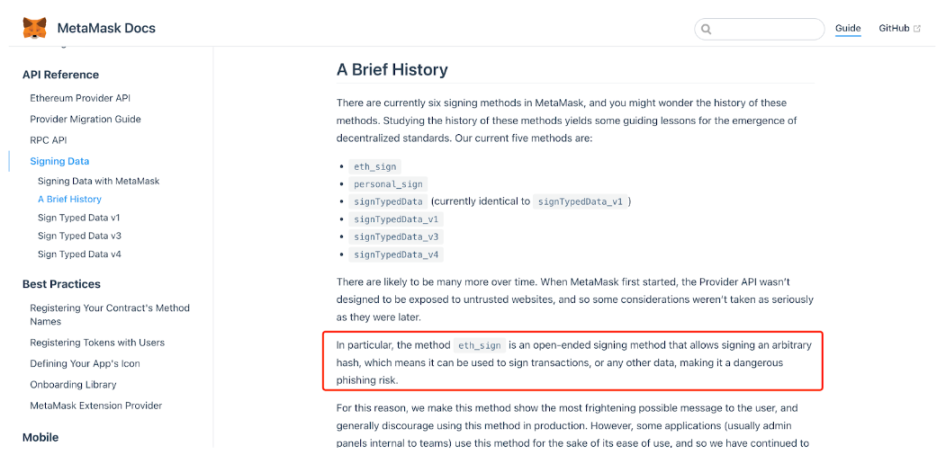
In other words, MetaMask currently has six signature methods (such as personal_sign), and only one method will cause a MetaMask warning, which occurs in the case of eth_sign signatures, because the eth_sign method is an open signature method, which allows any Hash Signing means it can be used to sign transactions or any other data, posing a dangerous phishing risk.
According to the official MetaMask documentation, the eth_sign method can sign any hash, and when we sign a transaction, we are essentially signing a string of hashes, but the encoding process in the middle is handled by MetaMask for us up. We can briefly review the process from coding to transaction broadcasting:
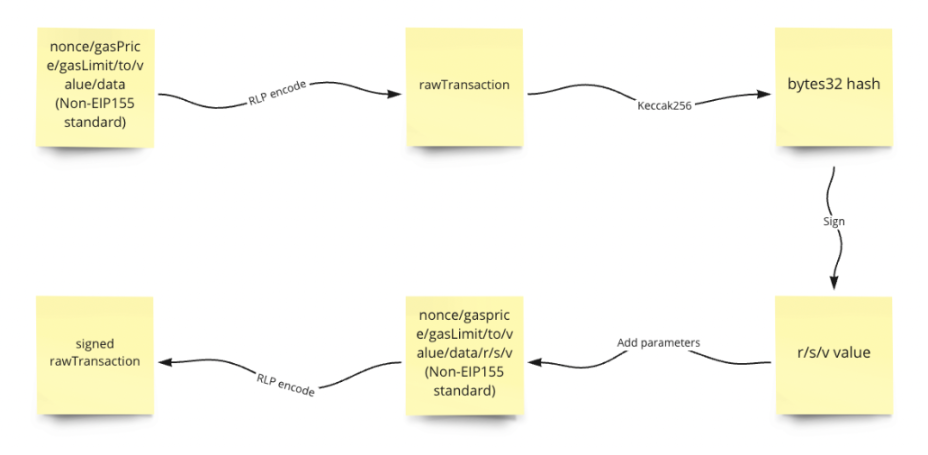
Before broadcasting the transaction, MetaMask will obtain the object of our transfer (to), the amount of transfer (value), the accompanying data (data), and the nonce, gasPrice, and gasLimit parameters that MetaMask automatically obtains and calculates for us, and perform RLP encoding to obtain Raw transaction content (rawTransaction). If it is a contract call, then to is the contract address, and data is the call data.
rlp = require(rlp);
// Use non-EIP115 standard
const transaction = {
nonce: ,
gasPrice: ,
gasLimit: ,
to: 0x,
value: ,
data: 0x
};
// RLP encode
const rawTransaction = rlp.encode([transaction.nonce, transaction.gasPrice, transaction.gasLimit, transaction.to, transaction.value, transaction.data]);
Then perform keccak256 hash on this content to get a string of bytes32 data, which is the data we need to sign.
// keccak256 encode
const msgHex = rawTransaction.toString(hex);
const msgHash = Web3.utils.keccak256(0x+ msgHex);
After we use MetaMask to sign this string of data, we will get r, s, v values, and then use these three values to perform RLP encoding with nonce/gasPrice/gasLimit/to/value/data to get the signed original transaction content Now, the transaction can be broadcasted at this time.
rlp = require(rlp);
const transaction = {
nonce: ,
gasPrice: ,
gasLimit: ,
to: ,
value: ,
data: ,
v: ,
r: ,
s:
};
// RLP encode
const signedRawTransaction = rlp.encode([transaction.nonce, transaction.gasPrice, transaction.gasLimit, transaction.to, transaction.value, transaction.data, transaction.v, transaction.r, transaction.s]);
As mentioned above, the eth_sign method can sign any hash, so it is natural to sign our signed bytes32 data. Therefore, the attacker only needs to obtain our address to analyze and query our account after we connect to the DApp, and then construct any data (such as: native token transfer, contract call) for us to sign through eth_sign.
This phishing method will be very confusing to users. MetaMask will intuitively display the data that the attacker wants us to sign for the authorized phishing we encountered in the past. As shown below, MetaMask shows that this phishing website induces users to authorize NFTs to malicious addresses.
Summarize
Summarize
Original link










