Source: SlowMist Technology
Background
According to the data from "Summary of Blockchain Security and Anti-Money Laundering in the First Half of 2023" published by SlowMist[1], there were a total of 10 incidents in the first half of 2023 where the stolen funds were fully or partially recovered after being attacked. The total amount of stolen funds in these 10 incidents was about $232 million, of which $219 million was returned, accounting for 94% of the stolen funds. In these 10 incidents, the funds were fully refunded in 3 cases.
Having stolen funds returned may become a new trend. Whether it is through offering bounties or negotiating with attackers to retrieve the stolen funds, there are mainly two ways to convey messages: one is to speak out on the project's media platform, and the other is for attackers and the project to communicate through on-chain messages.
For example, on March 13, 2023, the decentralized finance lending protocol Euler Finance was attacked, and the attacker profited about $197 million. On March 20, the attacker made an on-chain message to Euler[2], stating that they now want to "reach an agreement" with Euler. The attacker wrote: "We want everyone affected to be easier and we don't intend to keep something that doesn't belong to us. Let's establish secure communication and reach an agreement."
A few hours later, Euler replied on-chain[3], saying: "Message received, let's privately discuss via Euler Deployer address and one of your EOA on Blockscan, or through email contact@euler.foundation or any other channel you choose. Please reply with your preferred method."
Interestingly, on March 15th, 0x 2 af users sent on-chain messages to hackers [ 4 ], requesting the return of their life savings of 78 wstETH. The user stated, "Please consider returning 90% / 80%. I am just a regular user, and my life savings are only stored in Euler's 78 wstETH. I am not a whale or a millionaire. You cannot imagine how bad my situation is right now, all destroyed. I am sure that 20 million dollars is enough to change your life, and you can make many affected people happy again." Following that, the hacker sent them 100 ETH. Afterwards, many addresses mimicked the user's behavior and sent messages to the hacker.
Of course, there have also been cases of phishing messages on the chain. On March 22, 2023, after Euler hackers completed their attack, in order to confuse and evade investigation, they transferred 100 ETH to the Ronin hacker who had stolen over 625 million dollars. The Ronin hacker took advantage of the situation, responded with 2 ETH, and sent a message to the Euler hacker [ 5 ], asking them to decrypt an encrypted message. However, experts say that this message is a phishing scam, attempting to steal the private key of the Euler attacker's wallet. Is it really the case? SlowMist has written an analysis on this matter. If you're interested, you can check it out. A few minutes after the Ronin hacker wallet sent a message to the Euler hacker wallet, Euler Finance developers attempted to intervene with their own message [ 6 ] , warning the Euler hacker to be cautious of so-called decryption software and stating, "The simplest method is to return the funds." Euler's developers continued in another transaction [ 7 ], "Under no circumstances should you try to view that message. Do not enter your private key anywhere. Remember, your machine may also be compromised."
What is on-chain messaging?
As we all know, both Bitcoin and Ethereum mainnets are essentially distributed ledger systems that exist globally. Taking Ethereum as an example, there are currently over tens of thousands of Ethereum nodes replicating all the data on the Ethereum mainnet. This means that any message, transaction, or other information on the Ethereum mainnet is replicated tens of thousands of times, ensuring the immutability of blockchain information. Compared to the Bitcoin network, the fees on the Ethereum mainnet are relatively "cheaper", so most people choose the Ethereum mainnet as their first choice for leaving messages. As mentioned before, the essence of blockchain is a distributed ledger. When we conduct transfer transactions, we can also leave messages, which will be recorded in the ledgers of all nodes. These messages cannot be modified and will leave a permanent trace on the blockchain.
The first person to leave a message on the blockchain was Satoshi Nakamoto. On January 4, 2009, Satoshi Nakamoto left the headline of the day's The Times on the genesis block: "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks". Today, we can still find this message on the blockchain.
How to leave an on-chain message?
Basic: Unencrypted message
(1) Leave a message through https://app.mycrypto.com/send transfer
Connect your wallet, fill in the recipient address and transfer amount (which can be 0 ETH), enter the content you want to leave as a message after the "0x" in the Data field, then click Next, and finally Confirm.
Note: The message information needs to be in hexadecimal format, so you can use some conversion tools or websites to convert it in advance. For example:
(2) Transfer with mobile wallet message
You need to use an Ethereum wallet with some ETH (e.g., MetaMask, imToken wallet) to complete the transaction and pay the Gas fee. For example, open the imToken wallet, enter a transfer address for the transaction, click on Advanced mode, enter the message information in hexadecimal format, remember to start with "0x".
(3) Leave a message through Etherscan IDM [ 8 ]
With this tool, you don't need to input processed hexadecimal data in Input Data. You can directly enter the content you want to leave as a message, and it will automatically convert it into hexadecimal data for you. The result is displayed as follows:
Advanced: Encrypted message
Above, we have introduced unencrypted messages, and correspondingly, there are encrypted messages. Let's first look at an example:
(https://bscscan.com/tx/0xfa1fa7cdfa3c5fe2cfaf61e14caf4b5174302d3801b09bb650d3f90ec706c3e9)
Address 0x 313 sent a message on-chain to the address marked as TransitFinance Funds Receiver: "Please use the private key of your address to decrypt this message," along with a long piece of information that can only be viewed after decryption.
How is the encrypted on-chain message achieved?
(1) Encryption
First, search for the transaction hash by clicking on it through Etherscan:
Then, retrieve the raw transaction hexadecimal data of the transaction hash:
Next, obtain the public key based on the raw transaction hexadecimal data:
Then, input SecretMessage and publicKey and run the following code:
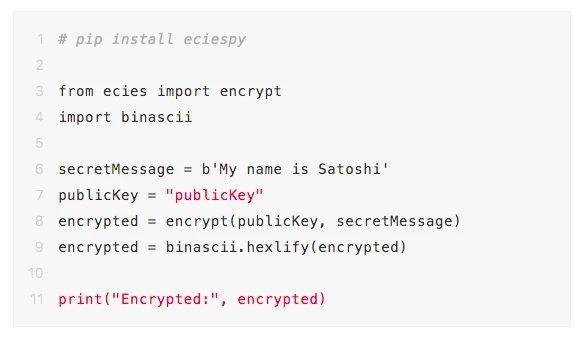
Finally, send using the above tools.
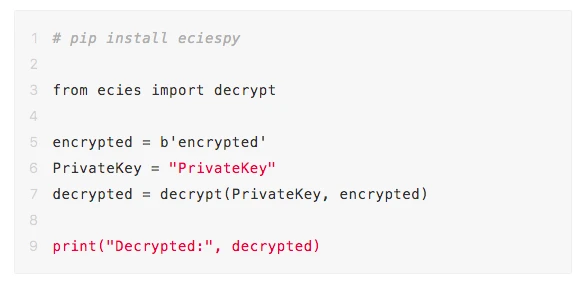
(2) Decryption
Input PrivateKey and encrypted, then run the following code:
SlowMist Assisting On-Chain Communication Example
As a blockchain threat intelligence and security company, SlowMist often receives requests for assistance from project teams or individual users. Here's an example. On October 2, 2022, the cross-chain trading platform aggregator Transit Swap was hacked, resulting in the theft of over $28.9 million in assets. At the request of the project team, we assisted in negotiations with the attacker.
The following is a partial transcript of the negotiation:
(https://bscscan.com/tx/0x7491671cfab5066d5a36299cf295e721611bae6ff61a847a32b11d1cf716c274)
(https://bscscan.com/tx/0xfa1fa7cdfa3c5fe2cfaf61e14caf4b5174302d3801b09bb650d3f90ec706c3e9)
According to the official statement on October 12, 2022, "White hat has returned funds worth $24 million".
Summary
This article mainly introduces the relevant knowledge and usage methods of on-chain messaging. On-chain messaging, as one of the anonymous communication methods, on the one hand, due to the immutability and transparency of on-chain information, it is also equivalent to passive scrutiny by the public, which may to some extent prevent one party from backtracking afterwards. On the other hand, this also provides a communication platform between victims and attackers, increases privacy, provides opportunities to reduce financial losses for victims, but also be cautious of phishing information in the messages.
In addition to on-chain messaging, users and project parties can still increase the possibility of recovering funds through the following methods:
Notify relevant institutions immediately: Report and appeal to local law enforcement agencies, financial regulatory agencies, and relevant blockchain project teams. Provide detailed information and evidence, and cooperate with the investigation of relevant institutions;
Contact the trading platform: If the funds were stolen on a specific trading platform, immediately contact them and provide detailed information about the incident. The trading platform may take measures to investigate and assist in resolving the issue;
Cooperate with the community: Make the incident public and cooperate with members of the relevant community to share information and experiences. Other users may provide useful information about attackers or attack techniques;
Seek professional help: Consult professional blockchain security companies or lawyers for legal and technical assistance. They can provide relevant advice and guidance to help recover funds as much as possible or take other appropriate legal measures. You can also contact the SlowMist AML team by submitting the form [9].
Of course, the most important thing is to take preventive measures to reduce the risk of fund theft, including using secure and reliable wallets and trading platforms; protecting private keys and access credentials; avoiding clicking suspicious links and downloading software from unknown sources; and maintaining security awareness and knowledge updates. Finally, it is highly recommended to read the "Blockchain Dark Forest Self-Help Manual" produced by SlowMist [10].
Reference links:
[1] https://www.slowmist.com/report/first-half-of-the-2023-report(CN).pdf
[2]https://etherscan.io/tx/0xcc73d182db1f36dbadf14205de7d543cfd1343396b50d34c768529aaab46a1c0
[ 3 ] https://etherscan.io/tx/0x9c25b6ca65c5bd0597a13ceae6f0d6edcef4b10279f338114550926ad0387ce4
[ 4 ] https://etherscan.io/tx/0xbe21a9719a4f89f7dc98419f60b247d69780b569cd8869c0031aae000f98cf17
[ 5 ] https://etherscan.io/tx/0xcf0b3487dc443f1ef92b4fe27ff7f89e07588cdc0e2b37d50adb8158c697cea6
[ 6 ] https://etherscan.io/tx/0x054409f252ac293a0ed34108b25e5906476817c5489bd3e98a5d3e1ee0825020
[ 7 ] https://etherscan.io/tx/0x1fd6d2e67a2ac4cf7c1718cc3058d5625171b95d66744801c97a4de54a41197b
[ 8 ] https://etherscan.io/idm
[9]https://aml.slowmist.com/recovery-funds.html
[10]https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md
[11] https://cryptobook.nakov.com/asymmetric-key-ciphers/ecies-example










