On September 7, 2023, the address (0x 13 e 382) suffered a phishing attack, resulting in a loss of over US$24 million. Phishing hackers used fund theft, fund exchange and decentralized fund transfer. Of the final lost funds, 3,800 ETH was transferred to Tornado.Cash in batches, 10,000 ETH was transferred to the intermediate address (0x 702350), and 1078, 087 DAI remains at the intermediate address (0x4F2F02) to this day.
This is a typical phishing attack. The attacker steals user assets by defrauding wallet authorization or private keys. It has formed a black industry chain of phishing + money laundering. At present, more and more fraud gangs and even national hackers are using phishing. The method is doing evil in the Web3 field and requires everyones attention and vigilance.
According to SharkTeam’s on-chain big data analysis platform ChainAegis (https://app.chainaegis.com/), we will conduct relevant analysis on the fraud process of typical phishing attacks, fund transfers, and on-chain behavior of scammers.
1. Phishing fraud process
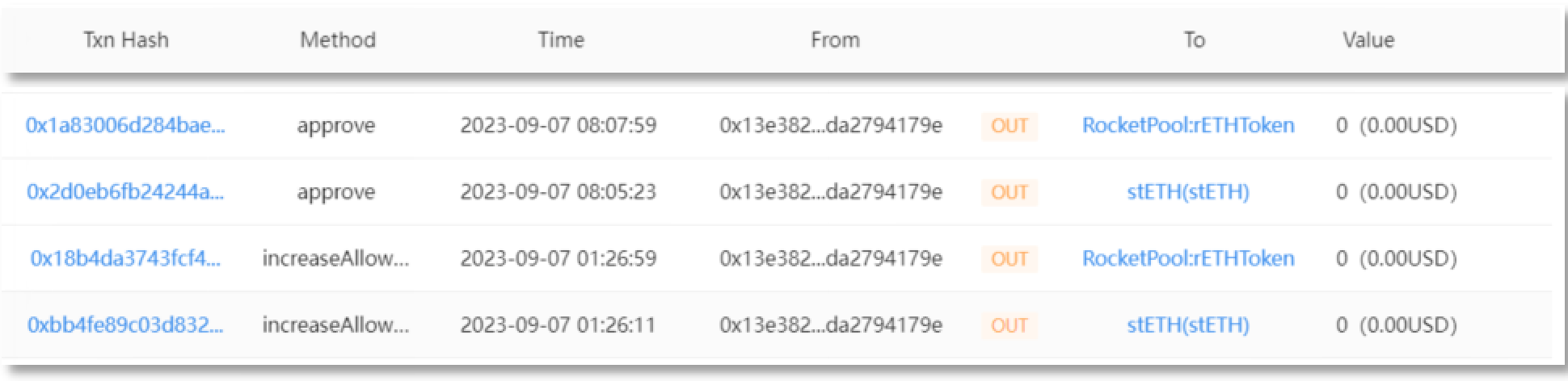
The victim address (0x13e382) granted rETH and stETH to the scammer address 1 (0x4c10a4) via Increase Allowance.
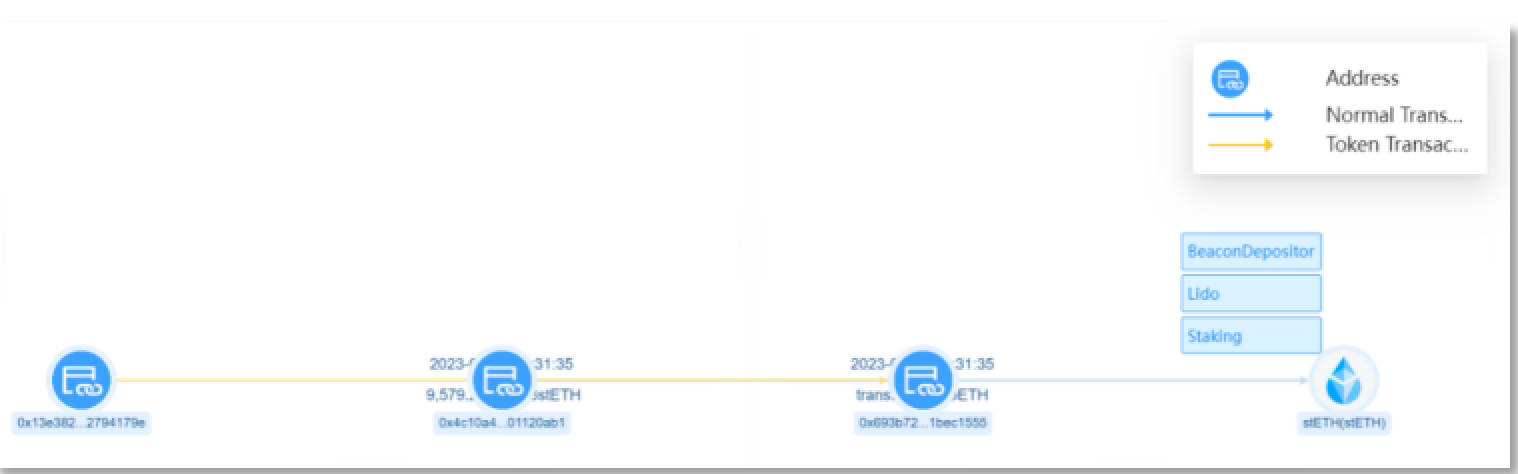
Scammer address 1 (0x4c10a4) transferred 9,579 stETH from the account of the victim address (0x13e382) to scammer address 2 (0x693b72), amounting to approximately $15.32 million.
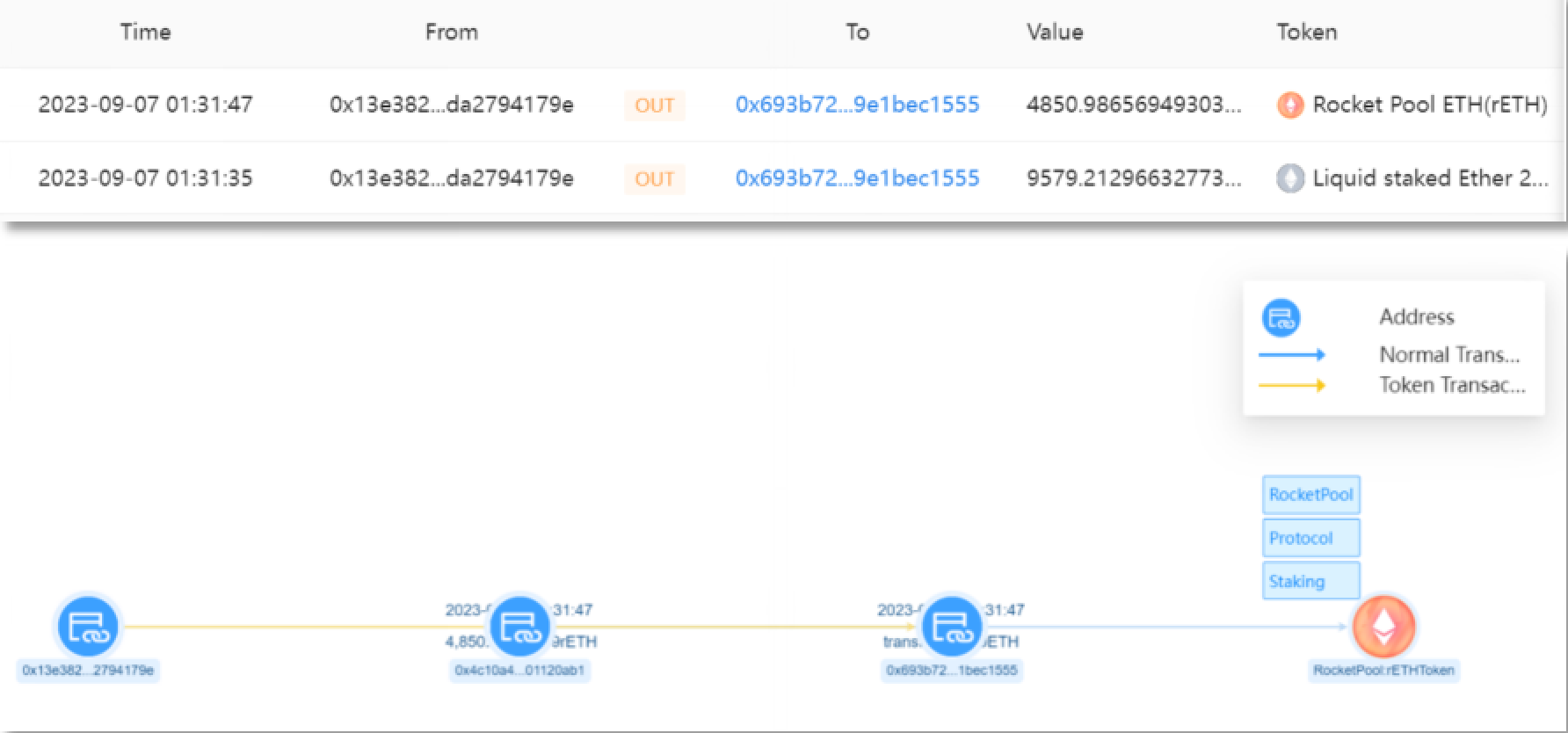
Scammer address 1 (0x4c10a4) transferred 4,850 rETH from the account of the victim address (0x13e382) to scammer address 2 (0x693b72), amounting to approximately $8.41 million.
2. Fund transfer tracking
2.1 Fund exchange
Exchange stolen stETH and rETH into ETH. Since the early morning of 2023-09-07, scammer address 2 (0x693b72) has conducted multiple exchange transactions on the Uniswap V2, Uniswap V3, and Curve platforms, converting all 9,579 stETH and 4,850 rETH into ETH, with a total exchange amount of 14 , 783.9413 ETH.
(1) stETH exchange:

(2) rETH exchange:

Part of the ETH is exchanged for DAI. Scammer address 2 (0x693b72) exchanged 1,000 ETH for 1,635,047.761675421713685327 DAI through the Uniswap V3 platform.
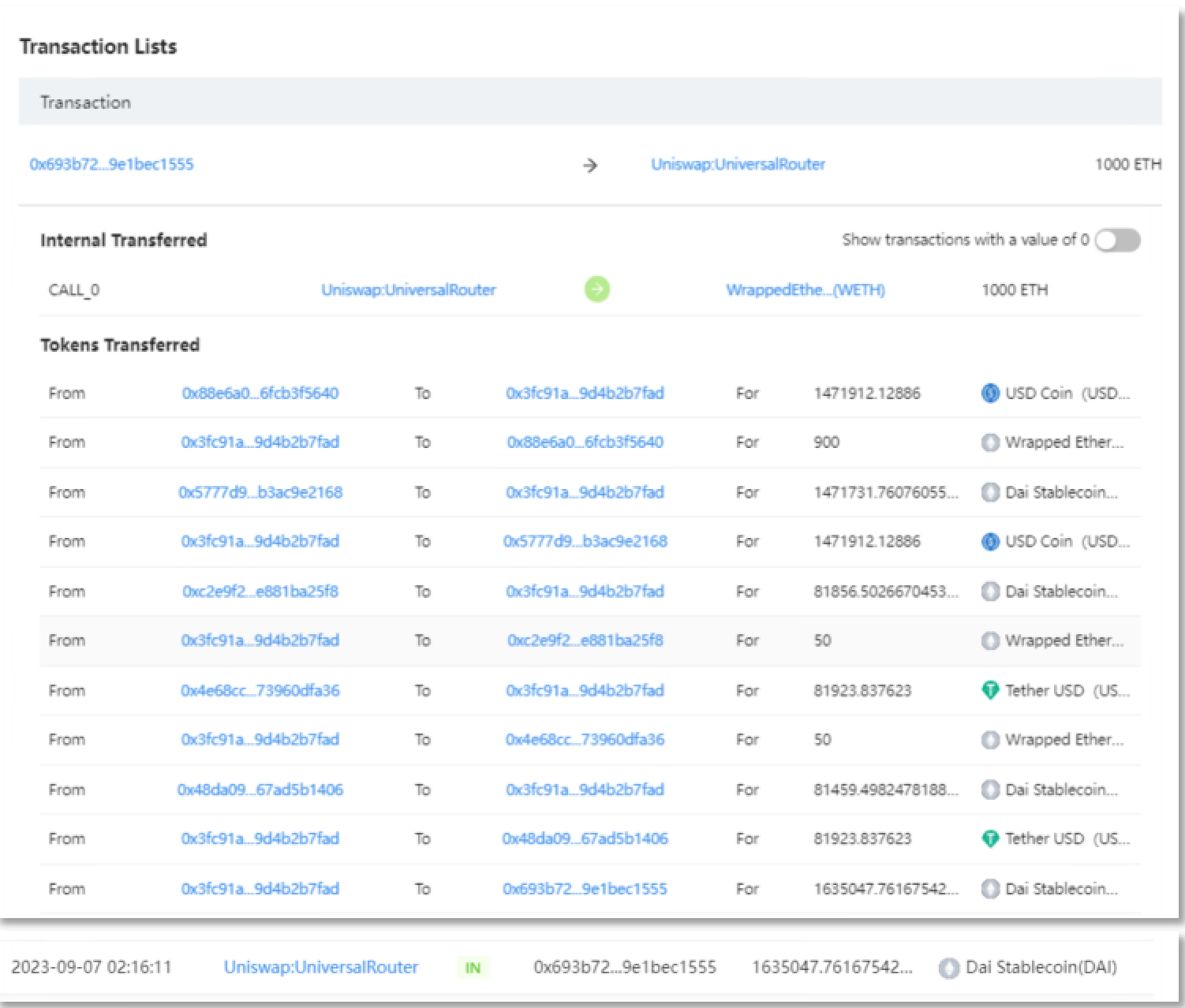
2.2 Fund transfer
The scammers used decentralized fund transfer methods to transfer the stolen funds to multiple intermediate wallet addresses, totaling 1,635,139 DAI and 13,785 ETH. Of these, 1,785 ETH were transferred to the intermediate address (0x4F2F02), 2,000 ETH were transferred to the intermediate address (0x2ABdC2), and 10,000 ETH were transferred to the intermediate address (0x702350). Additionally, the intermediate address (0x4F2F02) received 1, 635, 139 DAI the next day.
2.2.1 Intermediate wallet address (0x4F2F02) fund transfer
The address, which was transferred through layer 1 funds, holds 1,785 ETH and 1,635,139 DAI.
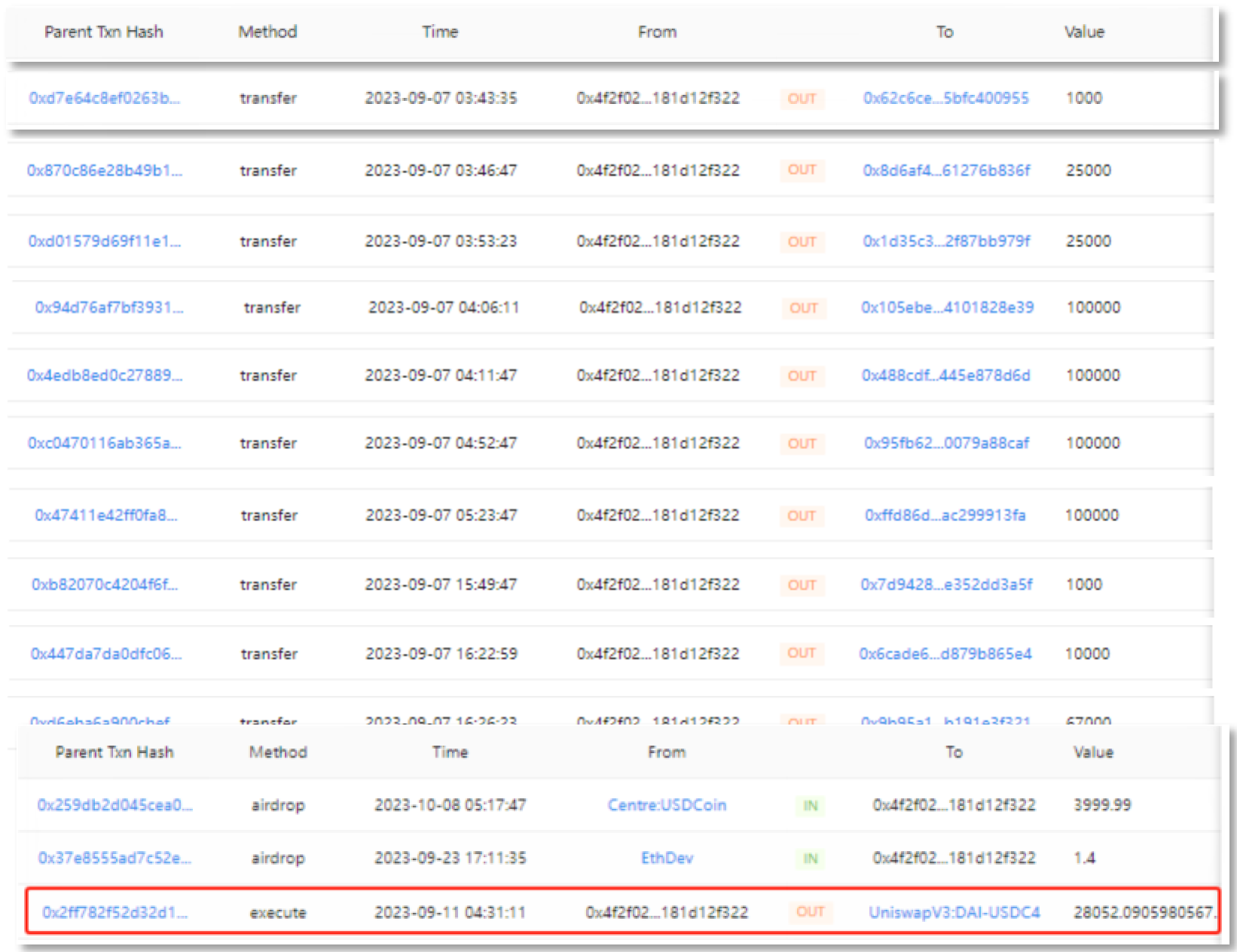
(1) Decentralized transfer of funds DAI, and exchange of small amounts into ETH
First, the scammer began to transfer 529,000 DAI through 10 transactions in the early morning of 2023-09-07. Subsequently, the first seven transactions totaling 452,000 DAI were transferred from the intermediate address to 0x4E5B2e (FixedFloat), the eighth transaction was transferred from the intermediate address to 0x6cC5F6 (OKX), and the last two transactions totaling 77,000 DAI were transferred from the intermediate address to 0xf1dA17 ( eXch).
Secondly, on September 10, 28,052 DAI was converted into 17.3 ETH through Uniswap V2.
After the transfer, the address finally had 1078,087 DAI of stolen funds remaining that had not been transferred out.
(2) ETH fund transfer

The scammer conducted 18 transactions from September 8 to September 11, transferring all 1,800 ETH to Tornado.Cash.
2.2.2 Intermediate address (0x2ABdC2) fund transfer
This address has 2, 000 ETH via a layer of funds transfer. First, this address transferred 2,000 ETH to an intermediate address (0x71C848) on September 11.
Subsequently, the intermediate address (0x71C848) made two fund transfers on September 11 and October 1 respectively, with a total of 20 transactions, each transferring 100 ETH, and a total of 2000 ETH was transferred to Tornado.Cash.

2.2.3 Intermediate address (0x702350) fund transfer
This address has 10,000 ETH via a layer of funds transfer. As of October 8, 2023, 10,000 ETH is still in the account at this address and has not been transferred.
3. Source of fraudulent funds
After analyzing the historical transactions of scammer address 1 (0x4c10a4) and scammer address 2 (0x693b72), it was found that there was an EOA address (0x846317) that transferred 1.353 ETH to scammer address 2 (0x693b72), and the EOA address funds The source involves hot wallet addresses with centralized exchanges KuCoin and Binance.
4. Summary
ChainAegis (https://app.chainaegis.com/) The platforms on-chain data analysis simply and clearly presents the entire process of phishing scammers on-chain fraud, as well as the current retention of fraudulent funds. After the scammers stole the funds from the victims address, they performed a series of fund exchanges and fund transfers, as shown in the figure below. A total of two fraud addresses were involved during the period: scammer address 1 (0x4c10a4) and scammer address 2 (0x693b72), and 4 intermediate addresses: intermediate address (0x4F2F02), intermediate address (0x2ABdC2), intermediate address (0x702350) and intermediate address ( 0x71C848). All are included in the blacklist address database by ChainAegis, and the intermediate addresses are monitored in real time.
About Us
SharkTeams vision is to secure the Web3 world. The team consists of experienced security professionals and senior researchers from around the world, who are proficient in the underlying theory of blockchain and smart contracts. It provides services including on-chain big data analysis, on-chain risk warning, smart contract audit, crypto asset recovery and other services, and has built an on-chain big data analysis and risk warning platform ChainAegis. The platform supports unlimited levels of in-depth graph analysis and can effectively fight against Advanced Persistent Theft (APT) risks in the Web3 world. It has established long-term cooperative relationships with key players in various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, polygon, OKX, Huobi Global, imToken, ChainIDE, etc.
Official website:https://www.sharkteam.org










