Original author: Shan, Thinking, SlowMist Security Team
background
On March 1, 2024, according to feedback from Twitter user @doomxbt, there were abnormalities in his Binance account and funds were suspected to have been stolen:

(https://x.com/doomxbt/status/1763237654965920175)
At first, this incident did not attract much attention, but on May 28, 2024, Twitter user @Tree_of_Alpha analyzed and found that the victim @doomxbt was suspected of installing a malicious Aggr extension with many good reviews in the Chrome store! It can steal all cookies on the websites visited by users, and someone paid some influential people to promote it 2 months ago.

(https://x.com/Tree_of_Alpha/status/1795403185349099740)
The incident has received more attention in the past two days. Some victims’ login credentials were stolen, and then hackers stole the victims’ cryptocurrency assets through cross-trading. Many users consulted the SlowMist security team about this issue. Next, we will analyze the attack in detail to sound the alarm for the crypto community.
analyze
First, we need to find the malicious extension. Although Google has already removed the malicious extension, we can see some historical data through snapshot information.
After downloading and analyzing, the JS files in the directory are background.js, content.js, jquery-3.6.0.min.js, and jquery-3.5.1.min.js.
During the static analysis, we found that background.js and content.js did not have too much complex code, nor did they have any obvious suspicious code logic. However, we found a link to a site in background.js, and the data obtained by the plug-in was sent to https[:]//aggrtrade-extension[.]com/statistics_collection/index[.]php.

By analyzing the manifest.json file, we can see that background uses /jquery/jquery-3.6.0.min.js and content uses /jquery/jquery-3.5.1.min.js, so lets focus on analyzing these two jquery files:

We found suspicious malicious code in jquery/jquery-3.6.0.min.js. The code processed the cookies in the browser through JSON and sent them to the site: https[:]//aggrtrade-extension[.]com/statistics_collection/index[.]php.
After static analysis, in order to more accurately analyze the behavior of the malicious extension sending data, we began to install and debug the extension. (Note: The analysis should be conducted in a brand new test environment, without any account logged in, and the malicious site should be changed to one that is controllable by ourselves to avoid sending sensitive data to the attackers server during the test)
After installing the malicious extension in the test environment, open any website, such as google.com, and then observe the network requests in the background of the malicious extension. It is found that Googles cookies data are sent to an external server:

We also saw cookies sent by the malicious extension on the Weblog service:
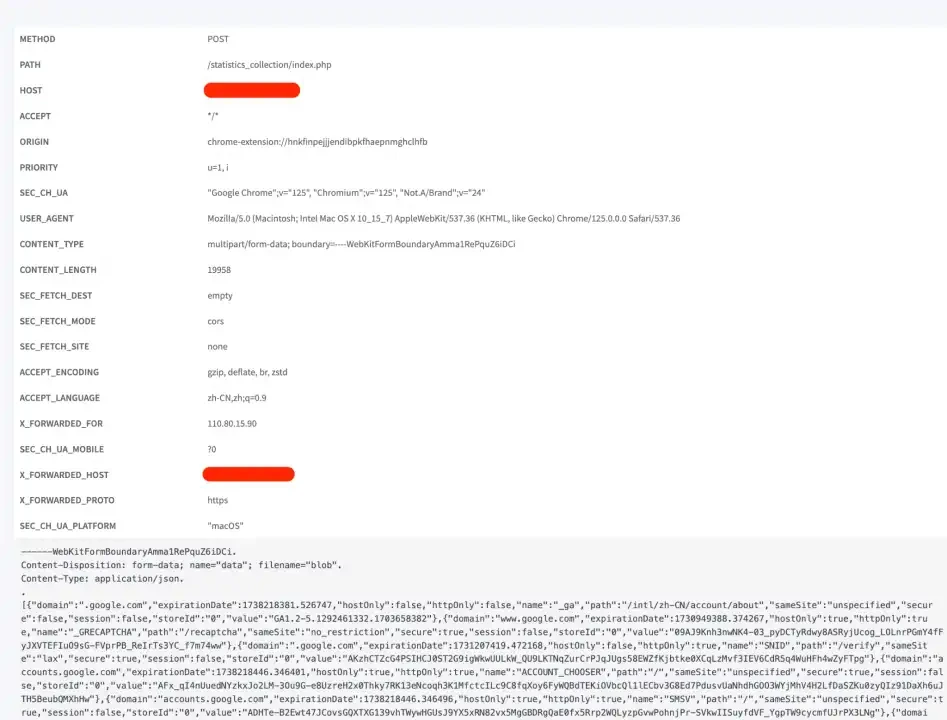
At this point, if an attacker obtains user authentication, credentials and other information and uses browser extensions to hijack cookies, they can conduct cross-trading attacks on some trading sites and steal users encrypted assets.
Let’s analyze the malicious link https[:]//aggrtrade-extension[.]com/statistics_collection/index[.]php.
Domain involved: aggrtrade-extension[.]com
Analyze the domain name information in the above figure:
.ru seems to be a typical Russian-speaking user, so it is likely to be a Russian or Eastern European hacker group.
Attack timeline:
Analyzing the malicious website aggrtrade-extension[.]com that impersonates AGGR (aggr.trade), we found that the hacker had been planning the attack three years ago:
4 months ago, hackers deployed the attack:

According to the InMist threat intelligence cooperation network, we found that the hackers IP is located in Moscow, using a VPS provided by srvape.com, and the email address is aggrdev@gmail.com.

After the deployment was successful, the hacker began to promote it on Twitter, waiting for the fish to take the bait. The rest of the story is well known to everyone, some users installed the malicious extension and then got stolen.
The following picture is the official reminder of AggrTrade:

Summarize
The SlowMist security team reminds users that the risk of browser extensions is almost as great as running executable files directly, so be sure to review carefully before installation. At the same time, be careful of those who send you private messages. Nowadays, hackers and scammers like to impersonate legitimate and well-known projects and defraud content creators in the name of funding and promotion. Finally, when walking in the dark forest of blockchain, always be skeptical and make sure what you install is safe.










