This article Hash ( SHA1 ): a3797a7829093777932a7a8c66e66358bfd8e356
No.: Lianyuan Security Knowledge No.016
In the growth process of Meme projects and ecological integration, Meme has always been regarded as a thermometer of ecological heat. The public chain ecology and Meme complement each other. In a certain period of time, the attention and traffic of the entire ecology will often be concentrated on a certain Meme. , Meme’s fame is the result of the joint efforts of the public chain team, public chain projects, public chain users and other parties. In the future, the Meme project on TON may be more prominent. Based on the user group of Telegram, TON has a Meme has a natural advantage that other public chains cannot match. It features a strong community culture and a broad user base. The trading enthusiasm and liquidity brought by these two can quickly increase the market value of token projects. TONs Notcoin is A successful example based on Meme characteristics. Although Notcoin is essentially a GameFi, it is also widely regarded as a Memecoin due to its wide user base and virality. With the success of Notcoin, many tokens imitating it have also emerged. However, this phenomenal spread is often accompanied by a large number of security issues, such as phishing websites impersonating the project to deceive users trust. While having fun, everyone needs to remain cautious.
Common security issues:
Contract vulnerabilities:
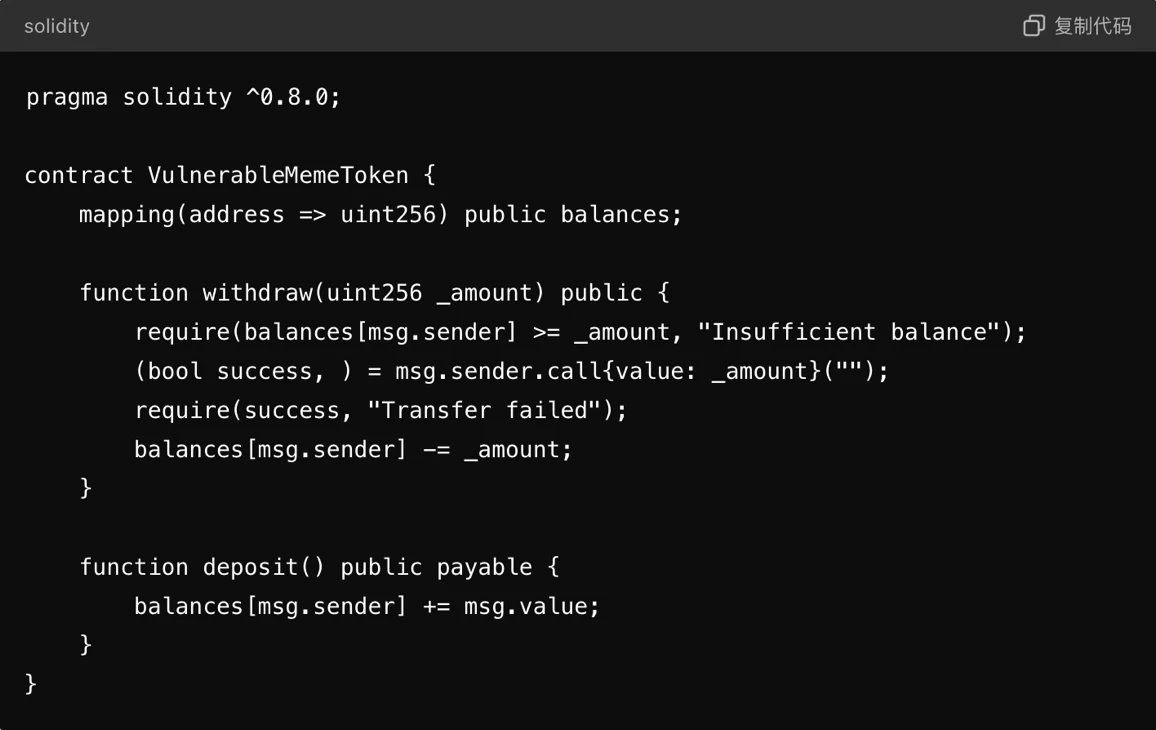
Smart contracts are the core of the meme coin project. Once a vulnerability occurs, it may lead to the theft or over-issuance of tokens. The following is a sample code of a common vulnerability - Reentrancy Attack:
In the above code, the external call msg.sender.call{value: _amount}() of the withdraw function has a potential reentrancy risk. In the attack scenario, the attacker can call withdraw again after receiving the funds, repeatedly Withdraw funds until the balance in the contract is drained.
Improper permissions management:
Many meme coin projects have deficiencies in permission management, and permissions for key operations such as minting and destroying tokens may not be effectively controlled. For example:
In this example, if the owner’s private key is leaked or mismanaged, an attacker could use this privilege to mint a large number of tokens and destabilize the market.
User Safety Guide Manual:
wallet:
Since TON is not an EVM public chain, a separate wallet is required. Among them, the most used are Wallet and Tonkeeper built in the Telegram applet, both of which are developed by TOP LAB. The difference is that Tonkeeper is a self-hosted wallet In this form, you need to keep your own mnemonic phrases and it supports Chrome plug-ins or mobile APP applications. Wallet is embedded in Telegram and operates as a mini-program. It is a hosted wallet that follows the Telegram account, but it needs to pass KYC identity verification before it can be used. In addition, Wallet now launches the TON SPACE function, which makes the wallet function more complete, can keep the mnemonic phrase by itself, and supports TON NFT or various Jettons tokens (similar to ERC 20/SPL Token, the feature of Wallet is that it can be more convenient Interoperate with various Telegram native applets.
Cross-chain bridges and centralized exchanges:
After preparing your wallet, you can choose to transfer funds to the TON chain from the official cross-chain bridge or a third-party bridge.
Official Bridge: https://bridge.ton.org/
LayerSwap: https://layerswap.io/app
Symbiosis: https://app.symbiosis.finance/
Rubic: https://app.rubic.exchange/
In addition to using cross-chain bridges, many centralized exchanges already support the deposit and withdrawal of $TON spot or $USDT on TON.
TON: OKX/ Bybit/ GATE/ MEXC/ Kucoin…
USDT on TON: Binance/ OKX/ Bybit/ GATE/ MEXC/ Kucoin…
On-chain applications:
DEX: STON.fi, Dedust.io
Aggregator: Mars.TonPlanets
LaunchPad: Tonraffles
Liquidity staking LSD: TonStakers $tsTON, Bemo $stTON
Derivatives Perpetual Contracts: Storm
NFT Marketplace + Lending: GetGems, Daolama
On-chain browser: TONViewer
Safety Check Tool:
The current mainstream inspection tools in the Ton ecosystem include:
Ton Inu inspection tool: Tg Bot, after entering the contract address, check whether LP is locked and whether the administrator authority is abandoned;
TON MINTER: A web tool that can check whether the administrator privileges have been given up. Because the security check tool is still underdeveloped and cannot 100% guarantee the security of tokens, users need to pay attention to the investment amount.
User precautions:
Our Lianyuan Security Team recommends that you:
Use security audited contract libraries: It is recommended to use audited standard contract libraries such as OpenZeppelin. These libraries have undergone extensive community review and testing and can significantly reduce security vulnerabilities in contracts.
Permission control and multi-signature mechanism: Strictly control the permissions of key operations. The multi-signature mechanism can ensure that multiple parties’ authorization is required when performing sensitive operations, thereby reducing the risk of single point errors.
Check project security audits: Security audits of smart contracts are an important means of discovering potential vulnerabilities. Users should choose projects that have been audited by reputable third-party security companies.
Implement real-time monitoring mechanism: Through blockchain monitoring tools, the transactions and abnormal behaviors of smart contracts are monitored in real time. Once abnormal activities are detected, such as abnormally large transactions or frequent failed transactions, alarms can be issued in time and countermeasures can be taken.
Conclusion
The Meme project has played an important role in promoting the blockchain ecosystem, but it has also brought many security challenges. Both developers and users should pay great attention to security issues. The ChainSource security team recommends that users take appropriate precautions to prevent By taking measures and using security tools, you can protect your assets and data security while enjoying the fun of the Meme project. With the development of blockchain technology and the joint efforts of the community, we believe that the future of the Meme project in the ton ecosystem will be brighter. .
Lianyuan Technology is a company focusing on blockchain security. Our core work includes blockchain security research, on-chain data analysis, and asset and contract vulnerability rescue. We have successfully recovered many stolen digital assets for individuals and institutions. At the same time, we are committed to providing industry organizations with project security analysis reports, on-chain traceability and technical consulting/support services.
Thank you for your reading. We will continue to focus on and share blockchain security content.










