Original | Odaily Planet Daily ( @OdailyChina )
Author | Asher ( @Asher_0210 )

Last night, the GMX platform , a leading DeFi protocol on the chain , suffered a major security incident. More than 40 million US dollars of crypto assets were stolen by hackers, involving WBTC, WETH, UNI, FRAX, LINK, USDC, USDT and other mainstream tokens. After the incident, Bithumb issued an announcement announcing that the deposit and withdrawal services of GMX will be suspended until the network is stable.
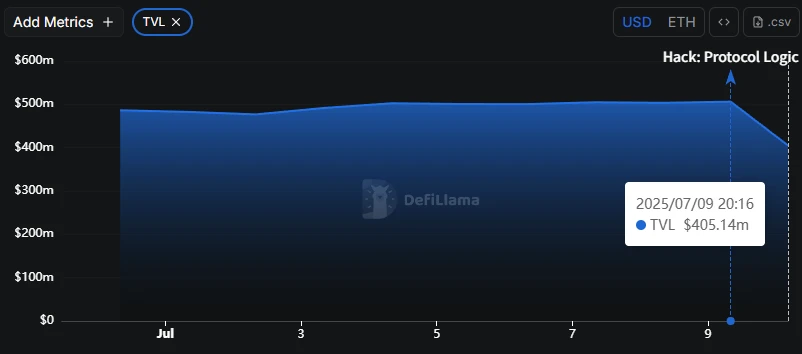
Affected by the theft, the GMX token fell by more than 25% in 4 hours, and the price once fell below $11, and is now at $11.8. According to DefiLlama data, GMX TVL fell from $500 million before the theft to $400 million, a short-term drop of up to 20%.
Next, Odaily Planet Daily will sort out the reasons for the GMX theft, the team’s response, and the latest trends of hackers.
Attacker exploits reentrancy vulnerability
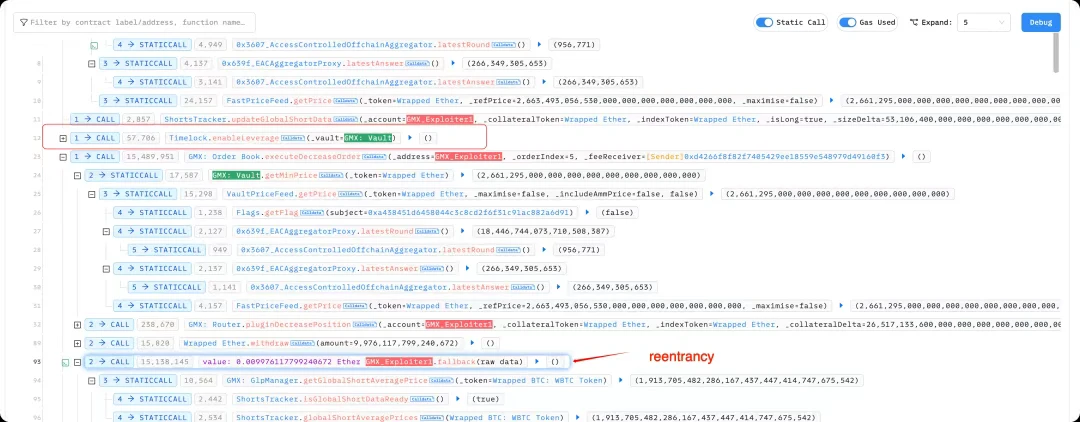
The root cause of the GMX theft is a reentrancy vulnerability in the core function executeDecreaseOrder. The first parameter of the function should have been an external account (EOA), but the attacker passed in a smart contract address, which allowed the attacker to re-enter the system during the redemption process and manipulate the internal state. Ultimately, the redeemed assets far exceeded the actual value of the GLP they held.
SlowMist partner and chief information security officer 23pds posted on the X platform that in GMX V1, the establishment of a short position will immediately update the global short average price (globalShortAveragePrices), which directly affects the calculation of total assets under management (AUM), and thus affects the valuation and redemption amount of GLP tokens.
The attacker took advantage of GMXs design of enabling the timelock.enableLeverage function during order execution (a prerequisite for opening large short positions) and triggered a reentrancy vulnerability in the executeDecreaseOrder function through a contract call. Using this vulnerability, the attacker repeatedly created short positions, artificially raising the global average short price without actually changing the market price.
Since AUM relies on this price calculation, the platform mistakenly included the inflated short losses in the total assets, causing the GLP valuation to be artificially inflated. The attacker then redeemed GLP and withdrew assets far in excess of his share, realizing huge profits.
Attack transaction example: https://app.blocksec.com/explorer/tx/arbitrum/0x03182d3f0956a91c4e4c8f225bbc7975f9434fab042228c7acdc5ec9a32626ef?line=93
GMX official response: The GLP liquidity pool of GMX V1 on Arbitrum was attacked by a vulnerability, and the GMX V2 version was not affected
In response to this major security incident, the GMX team has made an official response as soon as possible. It posted on the X platform that the GLP pool of GMX V1 on the Arbitrum platform was attacked by a vulnerability, and about $40 million of tokens have been transferred from the GLP pool to an unknown wallet. Security partners have participated in the investigation of this attack.
Currently, the Arbitrum and Avalanche platforms have disabled transactions for GMX V1 and the minting and redemption functions of GLP to prevent any further attacks, but the vulnerability does not affect the GMX V2 version or the GMX token itself.
Since GMX V1 has been attacked, users can reduce the risk by doing the following:
Disable leverage: Call Vault.setIsLeverageEnabled(false) to turn it off; if Vault Timelock is used, call Timelock.setShouldToggleIsLeverageEnabled(false).
Set maxUsdgAmounts of all tokens to 1: Use Vault.setTokenConfig or Timelock.setTokenConfig to prevent GLP from being further minted. It is worth noting that this value must be set to 1, not 0, because setting it to 0 means there is no upper limit, which will cause the vulnerability to continue to be exploited.
According to the latest update, the official said that it was confirmed that the attack was only aimed at GMX V1, and the GMX V2 version of the contract did not use the same calculation mechanism. However, out of caution, GMX has updated the upper limit of GMX V2 version tokens on Arbitrum and Avalanche, so the minting of new tokens in most liquidity pools is currently restricted. Once this restriction is lifted, you will be notified as soon as possible.
In addition, on-chain data shows that GMX has left a message to the hackers address, admitting that it has encountered a vulnerability in the GMX Vl version and is willing to provide a 10% white hat bounty. If the remaining 90% of the funds are returned within 48 hours, it will promise not to take further legal action.
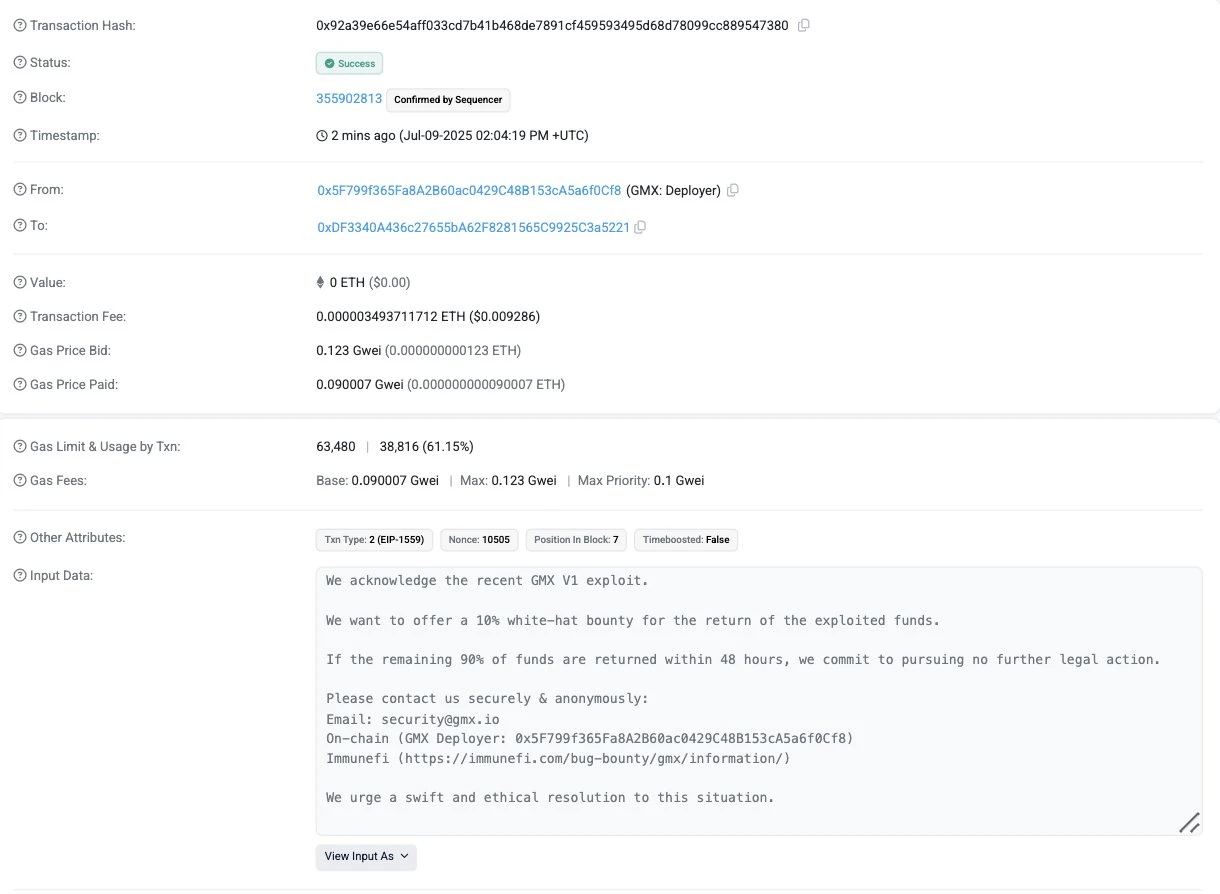
GMX has left a message to the hacker address and is willing to provide a 10% white hat bounty
Hackers have moved over $30 million to new addresses
Judging from the signs on the chain, this was a long-planned action. The hackers initial funds were transferred from the privacy mixing protocol Tornado Cash a few days ago, indicating that they had already made sufficient preparations for this attack.
After stealing more than $40 million in crypto assets, hackers quickly transferred more than $30 million in assets. According to on-chain data, the GMX hacker marked address (address: https://debank.com/profile/0xdf3340a436c27655ba62f8281565c9925c3a5221 ) has transferred 88 BTC (worth approximately US$9.8 million), more than 2,200 ETH (worth approximately US$5.85 million), more than 3 million USDC, and more than 1.3 million DAI to the new address 0x99cdeb84064c2bc63de0cea7c6978e272d0f2dae ; and transferred more than 4,300 ETH (worth approximately US$11 million) to the new address 0x6acc60b11217a1fd0e68b0ecaee7122d34a784c1 . In total, more than $30 million in funds have been transferred to other new addresses.
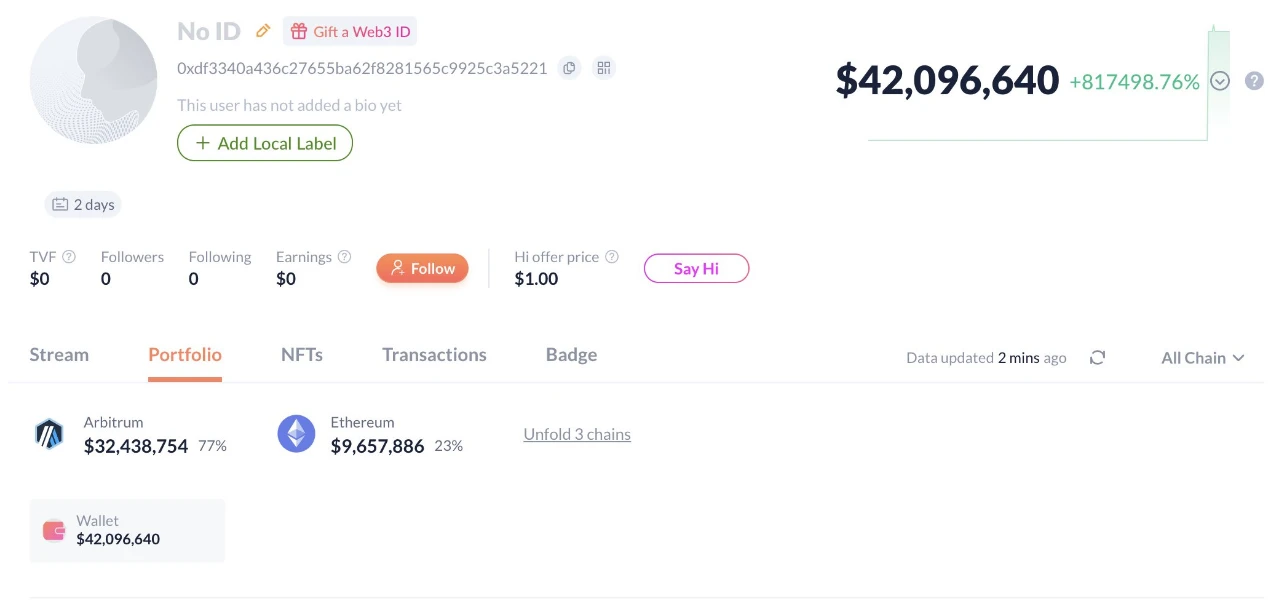
Hackers stole over $40 million in assets
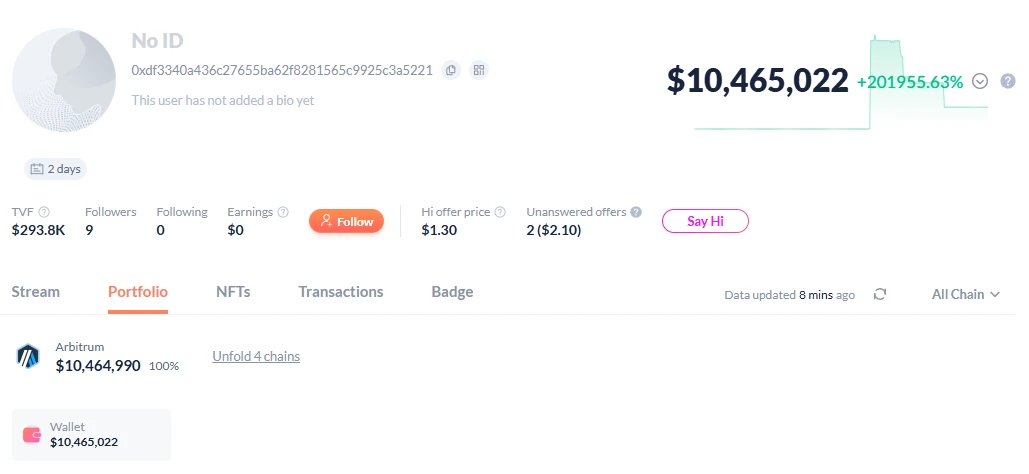
The remaining $10 million in funds in the current hacker address has not yet been transferred
Chain detective ZachXBT published an article on the X platform criticizing Circle for its inaction on the hacker behavior. He said that the GMX attack had occurred 1 to 2 hours ago, but Circle did not take any action against the hacker behavior. The attacker even used Circles cross-chain transfer protocol CCTP to transfer the stolen funds from Arbitrum to Ethereum.
summary
This theft not only revealed the key flaws of GMX V1 in caller permission verification, status update timing, and leverage mechanism design, but also once again sounded the alarm for the entire industry: in a system involving complex financial logic (such as leverage, dynamic pricing) and contract execution paths, any unprotected entry may evolve into the starting point of a black swan event.
It is worth noting that hackers have exchanged most of the stolen assets for cryptocurrencies that are more difficult to freeze, especially decentralized assets such as ETH and DAI, and dispersed the funds through multiple new addresses, further increasing the difficulty of tracking and recovering them. The 10% white hat bounty in exchange for exemption plan proposed by GMX also exposes the current reality of the lack of a unified legal accountability mechanism in the Web3 world.
For DeFi developers, perhaps the question they should think about more is not “how did the hacker succeed”, but whether sufficient mechanisms have been established to limit the occurrence of the most extreme attack paths when the system manages the real assets of users. Otherwise, no matter how perfect the product logic is, once there is a lack of security boundary design, it will eventually be difficult to escape the cost of systemic risk.










