Original author: YBB Capital Researcher Ac-Core

TLDR
Recently, Solana and Dialect jointly launched the new Solana concept Actions and Blinks to realize one-click Swap, Voting, Donation, Mint and other functions in the form of browser plug-ins.
Actions enable efficient execution of various operations and transactions, while Blinks ensures network consensus and consistency through time synchronization and sequential recording. These two concepts work together to enable Solana to achieve high-performance and low-latency blockchain experience.
The development of Blinks requires the support of Web2 applications, which first and foremost brings up issues of trust, compatibility, and cooperation between Web2 and Web3.
Compared with ActionsBlinks and FarcasterLens Protocol, the former relies on Web2 applications to obtain more traffic, while the latter relies more on the chain to obtain more security.
1. How Actions and Blinks work
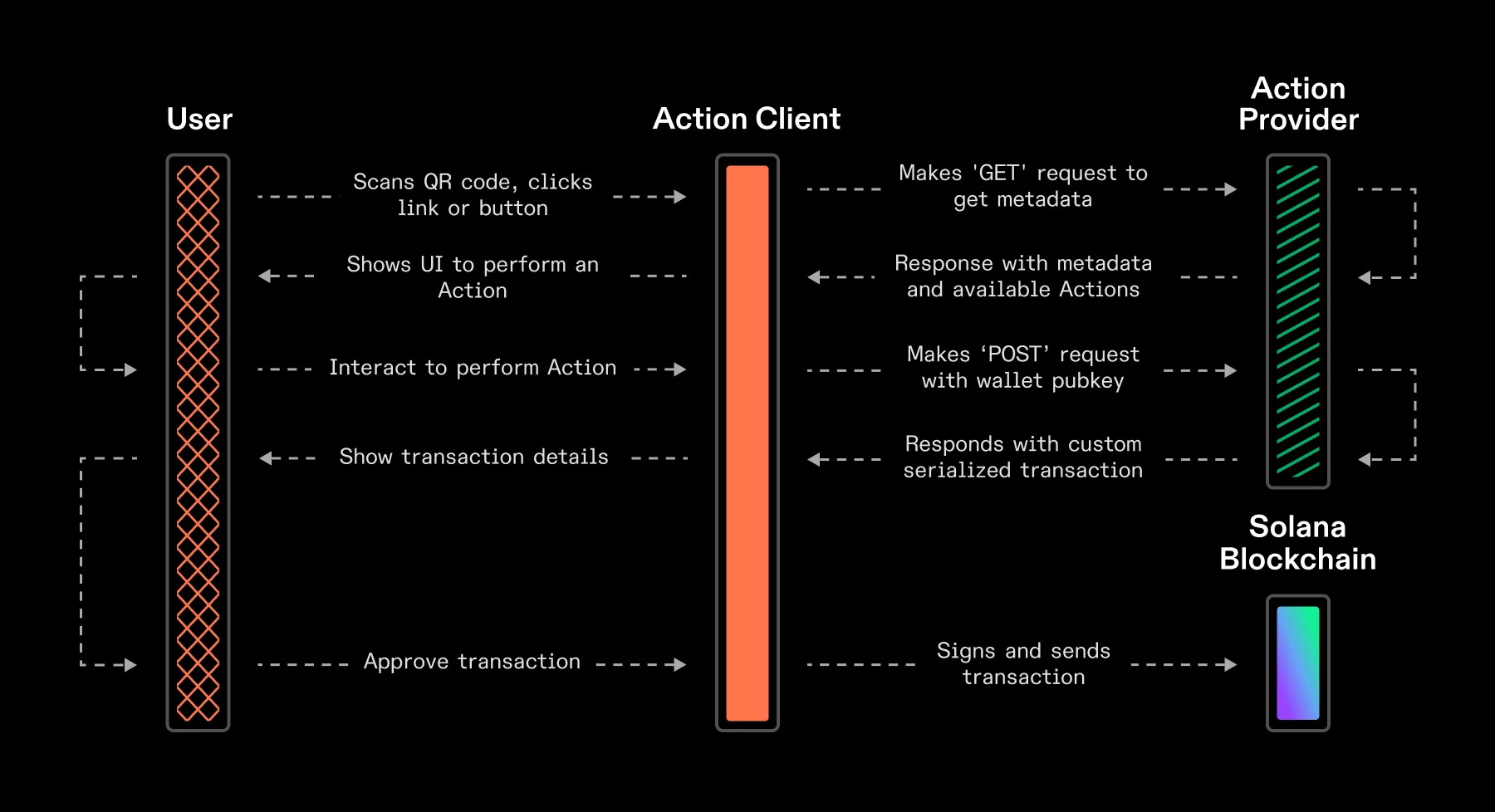
Image source: Solana docs (Solana Action execution process life cycle)
1.1 Actions (Solana Actions)
Official definition: Solana Actions are specification-compliant APIs that return transactions on the Solana blockchain that can be previewed, signed, and sent in a variety of different contexts, including QR codes, buttons + widgets (user interface elements), and websites on the Internet.
Actions can be simply understood as transactions to be signed. In the Solana network, Actions can be understood as an abstract description of the transaction processing mechanism, covering a variety of tasks such as transaction processing, contract execution, and data operations. In terms of applications, users can send transactions through Actions, including token transfers, purchases of digital assets, etc. Similarly, developers also use Actions to call and execute smart contracts to implement complex on-chain logic.
Solana uses the form of Transaction to handle these tasks. Each transaction consists of a series of instructions that are executed between specific accounts. By parallel processing and utilizing the Gulf Stream protocol, Solana forwards transactions to validators in advance, thereby reducing the delay in transaction confirmation. Through a fine-grained locking mechanism, Solana is able to process a large number of non-conflicting transactions at the same time, greatly improving the throughput of the system.
Solana uses Runtime to execute transactions and smart contract instructions, ensuring the correctness of the input, output, and state of transactions during execution. After the initial execution, the transaction will wait for block confirmation. Once the block is agreed by the majority of validators, the transaction is considered final. The Solana network is capable of processing thousands of transactions per second, with transaction confirmation times as low as less than 400 milliseconds. Thanks to the Pipeline and Gulf Stream mechanisms, the networks throughput and performance are further improved.
Actions do not just refer to certain tasks or operations, they can be transactions, contract executions, data processing, etc. These operations are similar to transactions or contract calls in other blockchains, but in Solana, Actions have their own unique advantages: First, efficient processing. Solana has designed an efficient way to process these Actions so that they can be quickly executed in a large-scale network. Secondly, low latency. Thanks to Solanas high-performance architecture, the processing latency of Actions is very low, allowing Solana to support high-frequency transactions and applications. Finally, flexibility. Actions can be used to perform a variety of complex operations, including the call of smart contracts, the storage and reading of data, etc. (See the extended link for more content).
1.2 Blinks (Blockchain links)
Official definition: Blinks converts any Solana Action into a shareable, metadata-rich link. Blinks enables clients that support Action (browser extension wallets, robots) to display more functionality to users. On the website, Blinks can immediately trigger a transaction preview in the wallet without jumping to the decentralized application; in Discord, the robot can expand Blink into a set of interactive buttons. This allows any web interface that can display a URL to achieve on-chain interaction.
In laymans terms, Solana Blinks converts Solana Action into a shareable link (equivalent to http). By enabling the relevant functions in supporting wallets such as Phantom, Backpack, and Solflare wallet, websites and social media can be transformed into places for on-chain transactions, allowing any website with a URL to directly initiate Solana transactions.
In summary, although Solana Action and Blink are permissionless protocols/specifications, compared with the solver solving process of intent narratives, they still require client applications and wallets to ultimately help users sign transactions.
The direct purpose of ActionsBlinks is to directly http link the on-chain operations of Solana to Web2 application products such as Twitter.
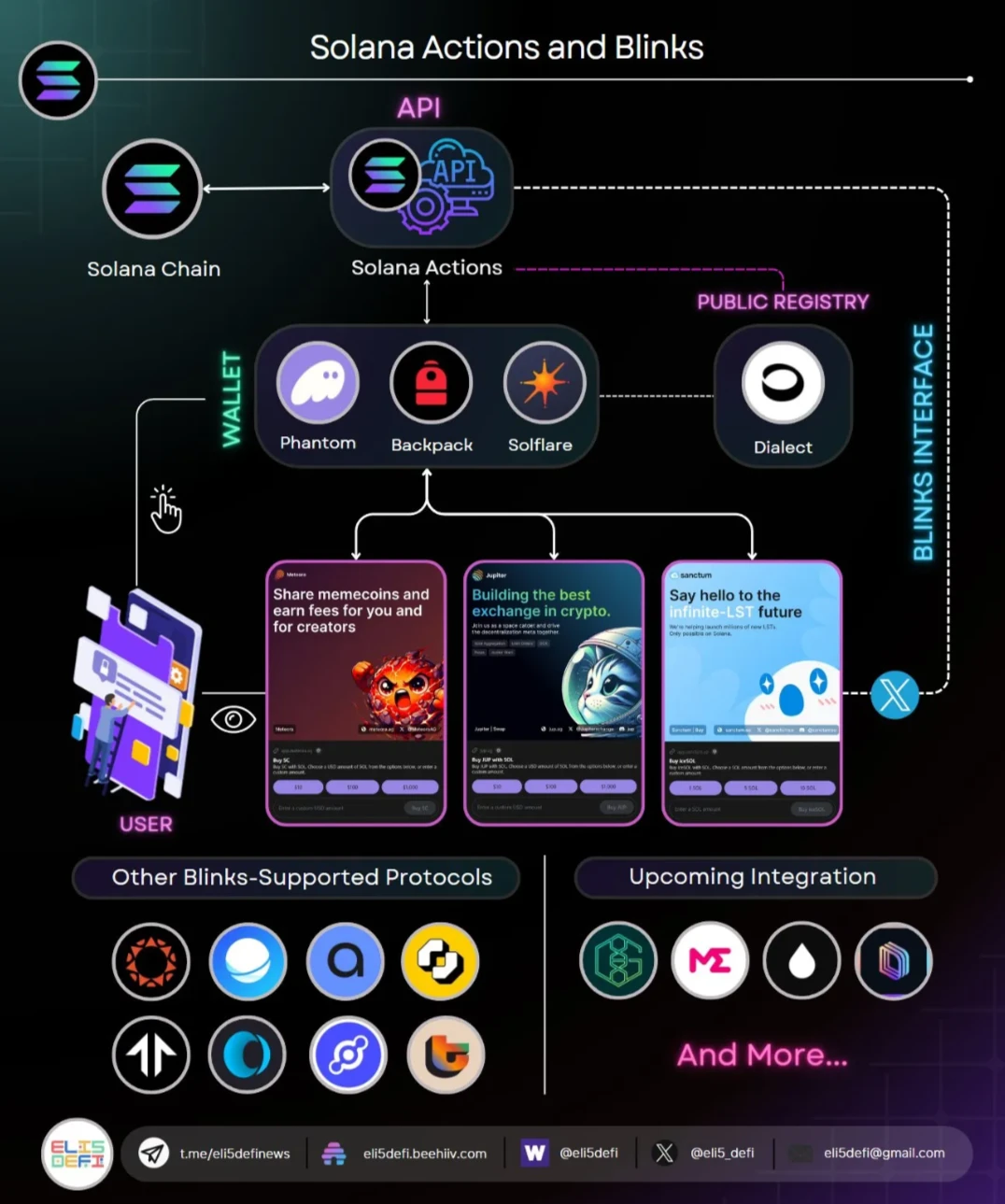
Image source: @eli 5 _defi
2. Decentralized social protocol based on Ethereum
2.1 Farcaster Protocol
Farcaster is a decentralized social graph protocol based on Ethereum and Optimism, which enables applications to connect with each other and users through decentralized technologies such as blockchain, P2P networks and distributed ledgers. It allows users to seamlessly migrate and share content between different platforms without relying on a single centralized entity. Its open graph protocol (when users post relevant links in social network posts, the protocol automatically extracts the content in the link and injects interactive features) allows the link content posted by users to be automatically extracted and converted into interactive applications.
Decentralized network : Farcaster relies on a decentralized network, avoiding the single point of failure problem of centralized servers in traditional social networks. It uses distributed ledger technology to ensure the security and transparency of data.
Public key encryption : Each user on Farcaster has a pair of public and private keys. The public key is used to identify the user, and the private key is used to sign the users operations. This method ensures the privacy and security of user data.
Data portability: User data is stored in a decentralized storage system rather than a single server. This way, users have full control over their data and can migrate it between different applications.
Verifiable identity : Through public key cryptography, Farcaster ensures that each users identity is verifiable. Users can prove their control over an account by signing.
Decentralized Identifier (DID) : Farcaster uses decentralized identifiers (DID) to identify users and content. DID is an identifier based on public key encryption, which is highly secure and tamper-proof.
Data consistency : To ensure the consistency of data in the network, Farcaster uses a consensus mechanism similar to blockchain (“posts” are nodes). This mechanism ensures that all nodes have a consensus on user data and operations, thereby ensuring the integrity and consistency of the data.
Decentralized Applications : Farcaster provides a development platform that allows developers to build and deploy decentralized applications (DApps). These applications can be seamlessly integrated with the Farcaster network to provide users with a variety of functions and services.
Security and Privacy : Farcaster emphasizes the privacy and security of user data. All data transmission and storage are encrypted, and users can choose to make their content public or private.
In Farcasters new Frames feature (different Frames are integrated with Farcaster and run independently), cast (analogous to posts, including text, pictures, videos, links, etc.) can be turned into an interactive application. These contents are stored in a decentralized network to ensure their persistence and immutability. When a post is published, each of its casts has a unique identifier to make it traceable, and the users identity is confirmed through a decentralized authentication system. As a decentralized social protocol, the Farcaster protocol can be directly and seamlessly connected to Frames by its clients.
2.2 The main principles include the following three aspects
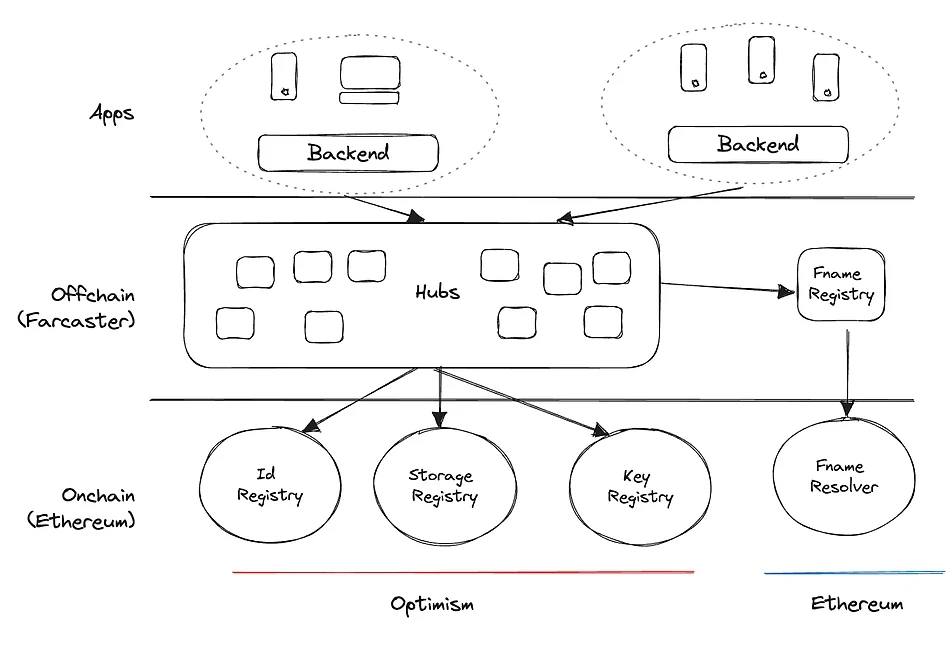
Image source: Architecture l Farcaster
The Farcaster protocol is divided into three main layers: Identity Layer, Data Layer (Hubs) and Application Layer. Each layer has specific functions and roles.
Identity Layer
Function: Responsible for managing and verifying user identities; providing decentralized identity authentication to ensure the uniqueness and security of user identities; specifically composed of four registries: ld Registry, Fname, Key Registry, and Storage Registry (see reference link 1 for details).
Technical principle: Using decentralized identifiers (DIDs) based on public key cryptography; each user has a unique DID to identify and verify the users identity; through the use of public and private key pairs, it ensures that only the user can control and manage their own identity information. The identity layer ensures that users can seamlessly migrate and verify their identities between different applications and services.
Data Layer - Hubs
Function: Responsible for storing and managing user-generated data, providing a decentralized data storage system to ensure the security, integrity and accessibility of data.
Technical principle: Hubs are decentralized data storage nodes distributed throughout the network; each Hub is an independent storage unit responsible for storing and managing a portion of the data. The data is distributed and stored between Hubs, and encryption technology is used to protect data security. The data layer ensures high availability and scalability of the data, and users can access and migrate their data at any time.
Application Layer
Function: Provides a platform for developing and deploying decentralized applications (DApps), supporting various application scenarios, including social networking, content publishing, messaging, etc.
Technical principle: Developers can use the APIs and tools provided by Farcaster to build and deploy decentralized applications; the application layer is seamlessly integrated with the identity layer and data layer to ensure user identity authentication and data management when using the application; decentralized applications run on a decentralized network and do not rely on centralized servers, which improves the reliability and security of the application.
2.3 Summary
The direct purpose of Solanas Actions Blinks is to open up traffic channels for Web2 applications. The potential impacts are as follows: From the users perspective: while simplifying transactions, it increases the risk of fund theft. From Solanas own perspective: it greatly enhances the traffic effect of breaking the circle, but there are still risks in application compatibility and support under the Web2 censorship system. Perhaps in the future, with the support of Solanas huge system, such as Layer 2, SVM, mobile operating systems, etc., there will be further development.
Compared with Solanas strategy, Ethereums Farcaster protocol weakens the traffic introduction of Web2, enhances the overall anti-censorship and security, and is closer to the native concept of Web3 under the Fracster+EVM model.
2.4 Lens Protocol

Image source: Lens Frens
Lens Protocol is also a decentralized social graph protocol that aims to provide users with full control over their social data and content. Through Lens Protocol, users can create, own and manage their own social graphs, and these graphs can be seamlessly migrated between different applications and platforms. The protocol uses non-fungible tokens (NFTs) to represent users social graphs and content, ensuring the uniqueness and security of the data. Lens Protocol and Farcaster, both located on Ethereum, also have some similarities and differences:
Same point:
User Control: Users have full control over their data and content in both.
Identity verification: Use decentralized identity (DID) and encryption technology to ensure the security and uniqueness of user identities.
difference:
Technology Architecture:
Farcaster: Built on Ethereum (L1), it is divided into the Identity Layer to manage user identities, the Data Layer (Hubs) decentralized storage nodes to manage data, the Application Layer to provide a DApps development platform, and uses offline Hubs for data dissemination.
Lens Protocol: Based on Polygon (L2), it uses NFT to represent users’ social graphs and content. All activities are stored in users’ wallets, emphasizing the ownership and portability of data.
Validation and Data Management:
Farcaster: Use distributed storage nodes (Hubs) for data management to ensure data security and high availability. Handles need to be updated every year, and delta graph is used to achieve consensus.
Lens Protocol: Personal data NFT ensures data uniqueness and security without the need for updates
Application Ecosystem:
Farcaster: Provides a comprehensive DApps development platform that integrates seamlessly with its identity layer and data layer.
Lens Protocol: focuses on the portability of user social graphs and content, supporting seamless switching between different platforms and applications.
Through the above comparison, we can see that Farcaster and Lens Protocol have similarities in user control and authentication, but have significant differences in data storage and ecosystem. Farcaster focuses more on hierarchical structure and decentralized storage, while Lens Protocol emphasizes the use of NFT to achieve data portability and ownership.
3. Which of the three can be the first to achieve large-scale application?
Through the above analysis, we can see that each of the three has its own advantages and challenges. Solana relies on its high performance and the ability to turn any website or application into a gateway for cryptocurrency transactions. It is the first to occupy the social media platform and quickly gain popularity and traffic advantages by relying on the advantage of Blinks to generate links. However, reliance on Web2 is also accompanied by the problem of exchanging traffic for security.
Lens Protocol was born in 2022 and has the longest history. Relying on the modular design and storage on the entire chain, it provides good scalability and transparency and has seized a wave of market opportunities. However, it may also face challenges in cost and scalability and the forgetting of market FOMO sentiment.
The advantage of Farcaster is that its underlying design is the most consistent with Web3 logic protocol compared to the previous two, and it has the highest degree of decentralization, but the challenges it brings are the difficulty of technology iteration and user management issues.
Extension Links:
(1) https://solana.com/docs/advanced/actions
Reference articles:










