The cryptocurrency industry has achieved its current status thanks to technological innovation. From Layer 2 to DePIN, from post-quantum encryption to ZKML, from homomorphic encryption 2.0 to adaptive consensus mechanism, these cutting-edge technologies and concepts are bursting with new vitality. However, in this crypto jungle built by code, the security line of defense is always under the test of sophisticated attacks.
In the large-scale on-chain Shura Field where scientists control MEV robots at millisecond speeds to accurately snipe transaction slippage, the smart contracts of the Pixiu disk weave a cage of funds that can only flow in but not out, phishing websites disguise malicious authorization pop-ups as tickets to freedom, Chinese tools hide hijacking clipboards, a family bucket of Trojans that steal private data, local dog projects change their Rug pulls, and star project owners delete and push content overnight and run away, safety is the most solid narrative to survive the bull and bear markets.
From the absurd farce of mnemonics running naked on the browser to the crypto security warnings shouted in the group chat, we often only pay attention to security issues when they occur, but this does not mean that it is not important. Because you can be unbelieving in evil when you are on the chain, but you must wear a bulletproof vest. Being a little timid can help you live longer. We must realize that security DNA must evolve rapidly and trading tools must be chosen correctly - in a decentralized world, real security depends on a stronger trust infrastructure. Today, lets talk about the security capabilities of the OKX Web3 wallet in my eyes, covering token detection, authorization detection, DApp detection, private key protection, etc., and how it protects our on-chain transactions and asset security.
1. Malicious Token Detection
The most common thing we deal with is a variety of tokens, but we are unable to identify their risks. Common malicious tokens include: Pixiu coins, phishing airdrops, and medium-risk coins. The first category is Pixiu coins. These tokens can be bought on the surface, but cannot be sold smoothly, or they need to pay too high taxes when they are sold, or they may even be unable to trade because the user is blacklisted. For example, after buying, the user finds out that he needs to pay a 95% sales tax, or when trying to withdraw cash, he finds that the address has been blacklisted and cannot be traded.
The second type is junk airdrops, where the tokens themselves have no value, but may have the same name as valuable tokens, and are precisely airdropped to a small number of users for targeted phishing. Users mistakenly believe that they have obtained valuable coins, but after buying them, they find that the token pool is not deep enough, resulting in being locked in when exchanging, or the tokens themselves are Pixiu disks that cannot be sold, or hackers drain the fund pool in an instant, leaving users with nothing but air.
When I received the above two types of malicious tokens using the OKX Web3 wallet, I found that they were automatically hidden, effectively preventing me from being misled by these junk tokens to trade. At the same time, the wallet will set the price of worthless tokens to zero, helping me quickly identify their risks and avoid careless transactions. In addition, if I try to trade these tokens through OKX DEX, the system will pop up a risk warning and block the transaction, further protecting the security of my assets.
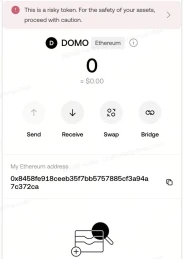
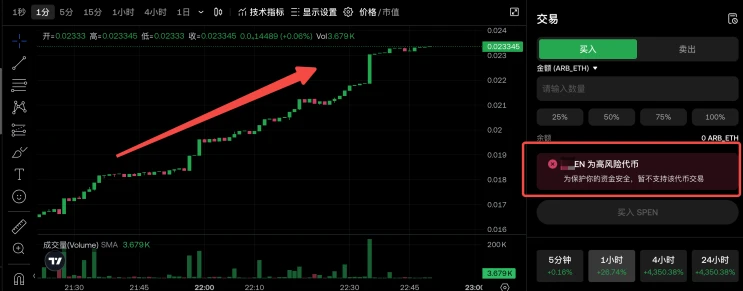
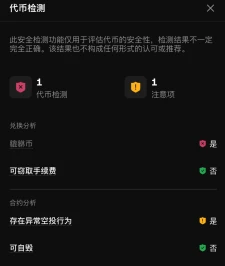
OKX Web3 Risk Token Transaction Protection Diagram
The third category is medium-risk coins, including low-liquidity coins, wash-trading coins, blacklisted coins, etc. Low-liquidity coins mean that it may be difficult to sell in the short term after purchase; wash-trading coins inflate trading volume through frequent transactions to attract traders and eventually withdraw liquidity; blacklisted coins only allow specific users to trade, misleading other traders. When encountering such a situation, the OKX Web3 wallet will set the price of the third-category risk token to zero and warn me of the risk.
2. KYS Risk Identification
In addition to token transactions, the most common scenario for us to interact on the chain is to access DApp. Generally speaking, the steps for Web3 wallets to interact with DApps are usually upgraded as follows: connecting wallets, authorization, transaction signatures, and confirming transactions.
We often encounter risks in the authorization process. For example, when trading tokens on a DEX, we need to authorize the DApp to access specific tokens in our wallet and allow the DApp to perform operations on our behalf by signing transactions. In this way, we can avoid the need to re-authorize each time. The signing process is actually a confirmation of the transaction quantity, price, etc., to ensure that each operation is in line with our intentions.
The KYS risk identification function of the OKX Web3 wallet is similar to the traditional KYC mechanism, but it focuses more on monitoring and analyzing our transaction behaviors, especially transaction authorization and signatures, to identify abnormal or malicious activities. Next, I must talk to you about those authorization risk scenarios and the protection function of the OKX Web3 wallet at critical moments.
Scenario 1: Transferring to a “Black Address”
Have you ever had this experience? When transferring money, you didn’t think much and just entered an address. In fact, I almost transferred money to a “normal black address”. Fortunately, the OKX Web3 wallet popped up a striking red warning at the critical moment - “This transaction is risky”, which avoided a loss.
However, what is more terrifying than ordinary black addresses are black contracts. These addresses are often disguised as official contracts of popular projects, with the same token names and icons, making it difficult for us to distinguish the real from the fake. Unlike the simple prompts of ordinary black addresses, when the OKX Web3 wallet detects interaction with a black contract, it will directly intercept the transaction to ensure the safety of our assets and avoid the risks caused by misoperation.
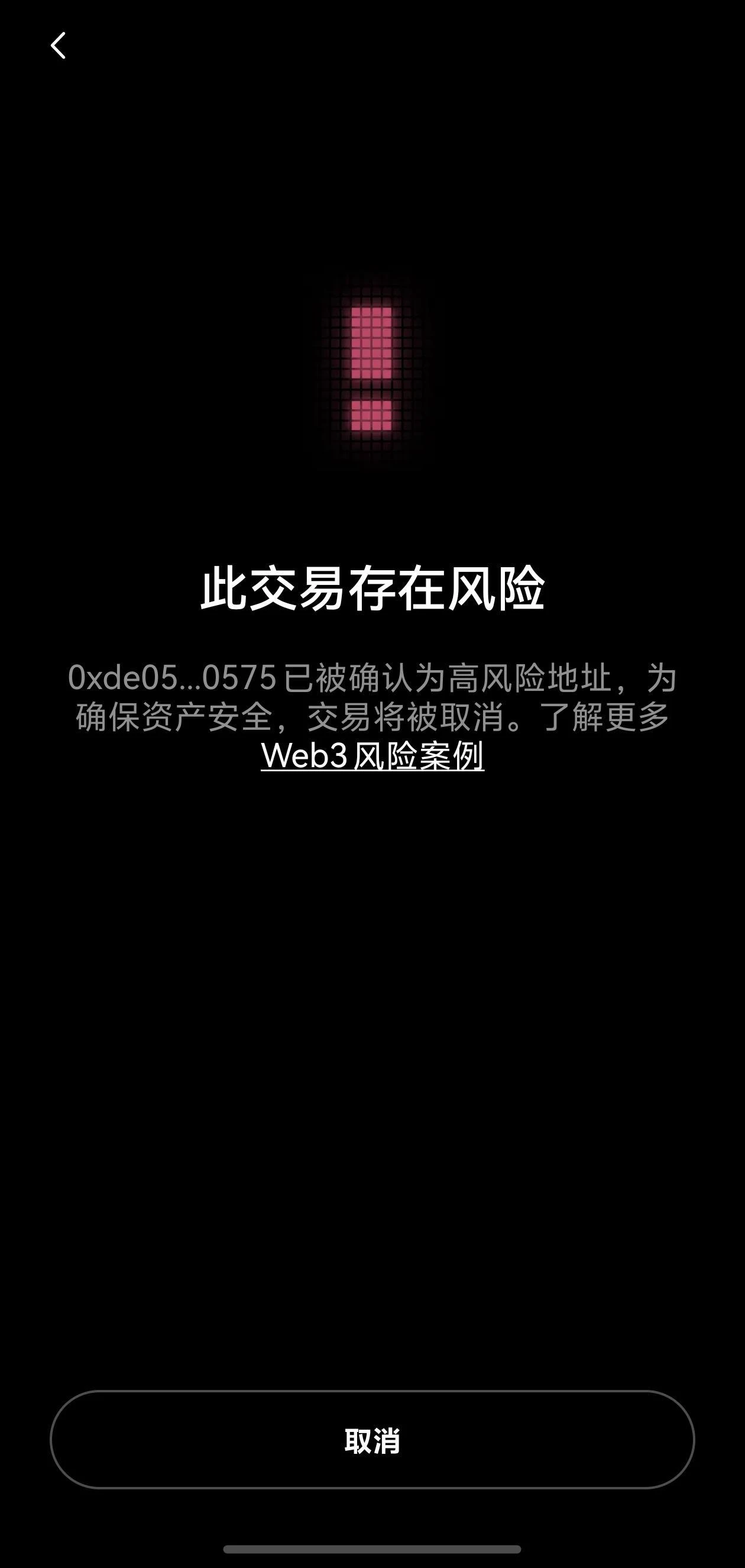
OKX Web3 wallet intercepts black contract interaction diagram
Scenario 2: Authorization is incorrectly granted to the EOA account instead of the DApp contract address
When we perform authorization operations, the authorization object should usually be the smart contract of the DApp, not the EOA account. If we authorize an EOA account, it means that our wallet is authorized to another wallet/person, which is likely to cause asset risks. When I try to authorize an EOA account, the OKX Web3 wallet will issue an alarm, reminding me to carefully check the authorization object to avoid asset losses due to trusting the wrong object.

OKX Web3 Wallet EOA Authorization Interception
Scenario 3: Transferring to a similar address
Scammers often commit fraud by creating addresses that are highly similar to our commonly used interactive addresses, such as changing 0x 1230...321 to 0x 1238...32, inducing us to transfer funds to the wrong address. There is almost no difference to the naked eye, and many times we are deceived without paying attention. Fortunately, the OKX Web3 wallet will detect the similarity of the transfer address and issue a risk warning when an anomaly is found, helping us confirm the transfer target and avoid transferring funds to the scammers due to negligence.
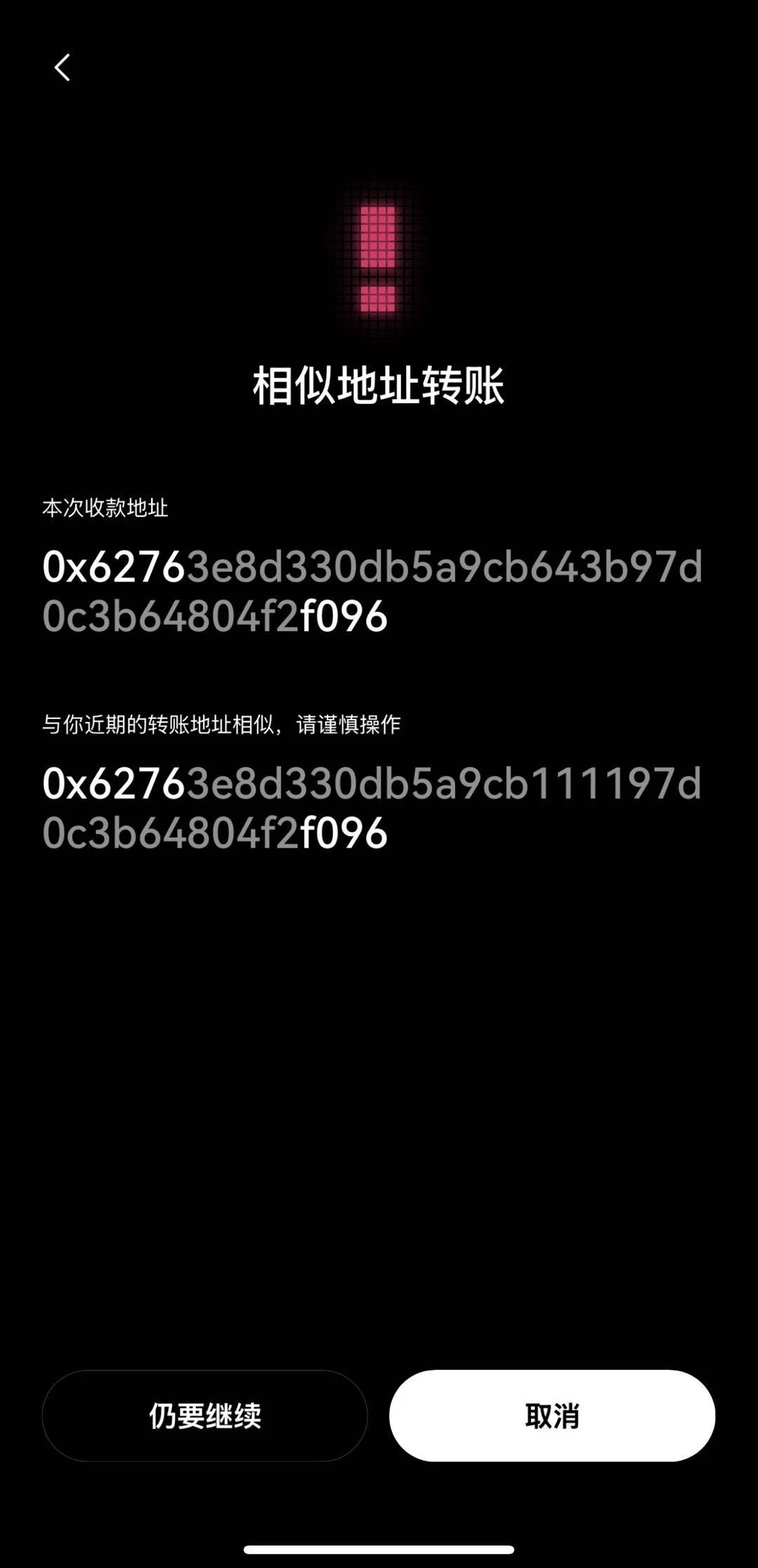
Diagram of the alarm when OKX Web3 wallet transfers funds to similar addresses
Scenario 4: ETHSign Signature Risk
ETHSign is a signature method commonly used for Ethereum authorization or transaction confirmation. However, if the signature content is maliciously tampered with or exploited, we may inadvertently sign unsafe transactions, resulting in asset losses. To avoid such risks, the OKX Web3 wallet will issue risk warnings in a timely manner when users perform signature operations to help users identify potential threats to signature content and ensure the security of each operation.
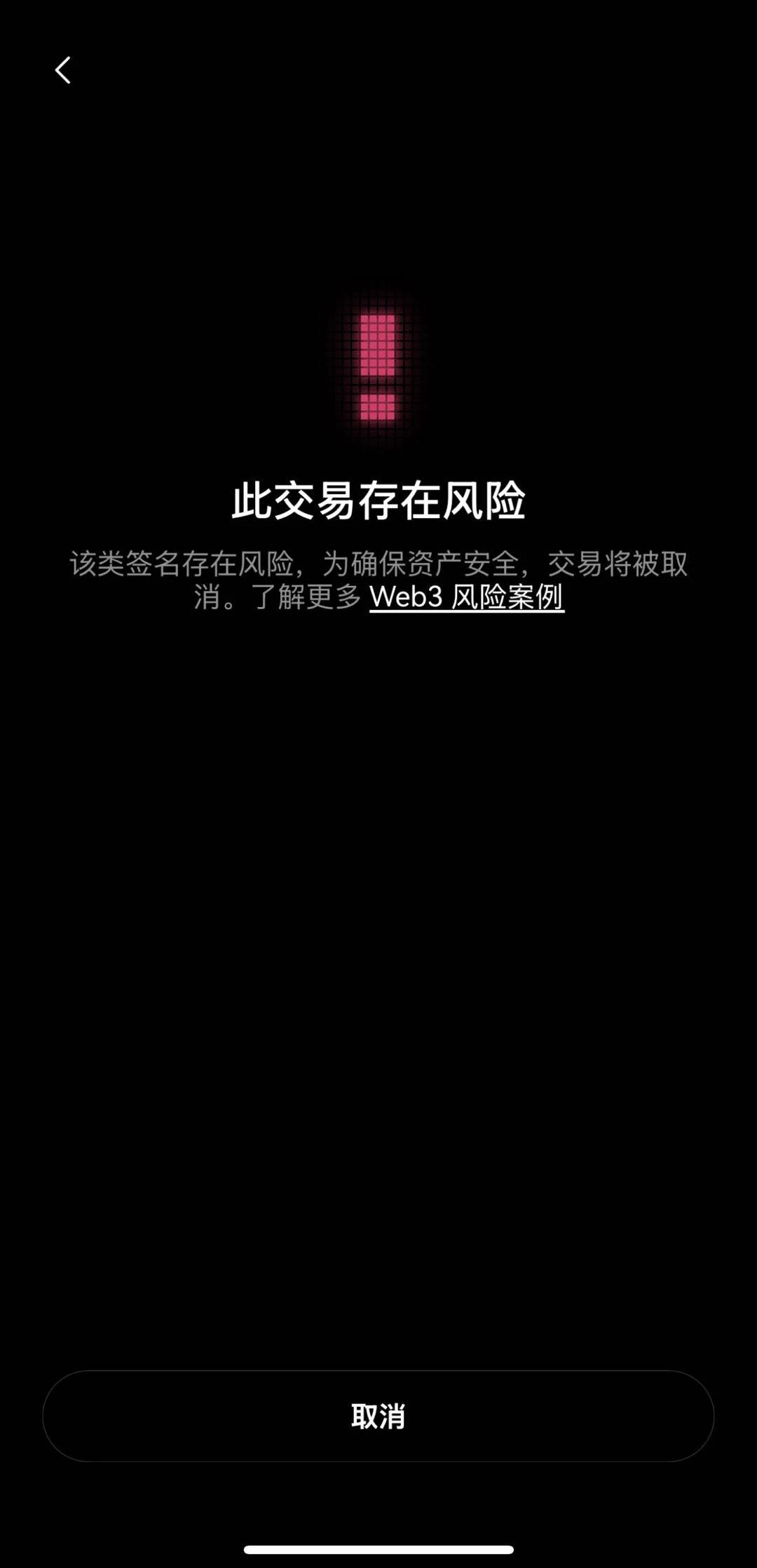
OKX Web3 Wallet ETHSign Signature Risk Warning Diagram
Scenario 5: “HexData Hijacking” on the TRON Chain
On the Tron network, malicious actors may tamper with the transaction content by modifying HexData (the hexadecimal data of the transaction), causing us to perform unexpected operations. The OKX Web3 wallet monitors the modification behavior of HexData and issues risk warnings when anomalies are found to protect the security of our transactions on the Tron network.

OKX Web3 wallet monitors HexData modification behavior diagram
Scenario 6: Buying “Malicious Tokens”
There is also the purchase of malicious tokens. Let me explain briefly that malicious tokens may have built-in backdoors or traps, such as being unable to sell or automatically transfer user assets, and we are likely to lose funds after purchasing. When we try to buy suspicious tokens, the OKX Web3 wallet will issue a prompt and provide the option to cancel the transaction to help users avoid falling into the trap of token fraud.
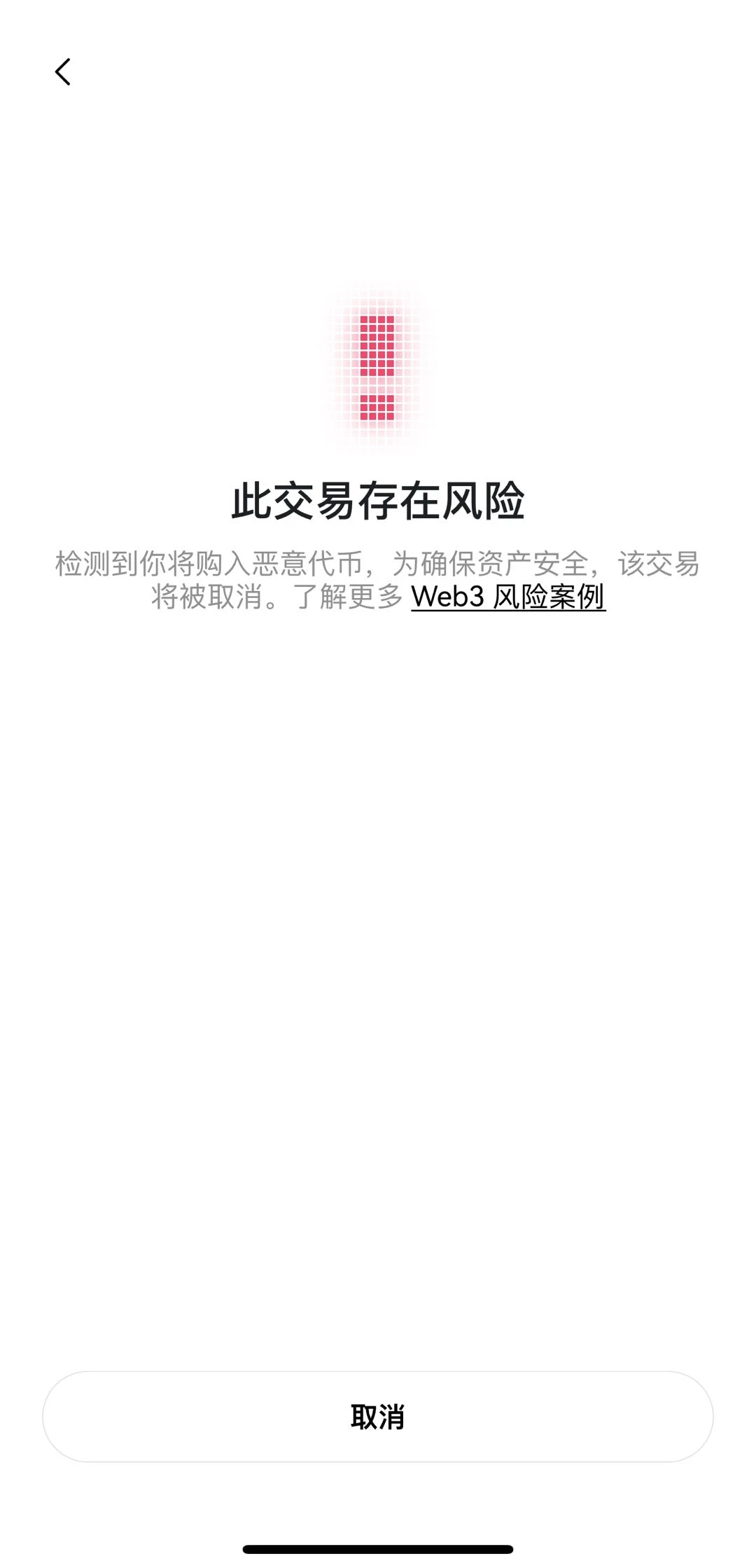
OKX Web3 wallet warns of risks of purchasing “malicious tokens”
Scenario 7: Solana changes account Owner
This year, playing MEME on the Solana network is very popular. If the Owner of our account is maliciously modified, it is very likely that we will lose control of the account and our assets will be stolen. The OKX Web3 wallet will monitor the modification behavior of the account Owner and issue a prompt when a risk is detected to ensure the security of our account.
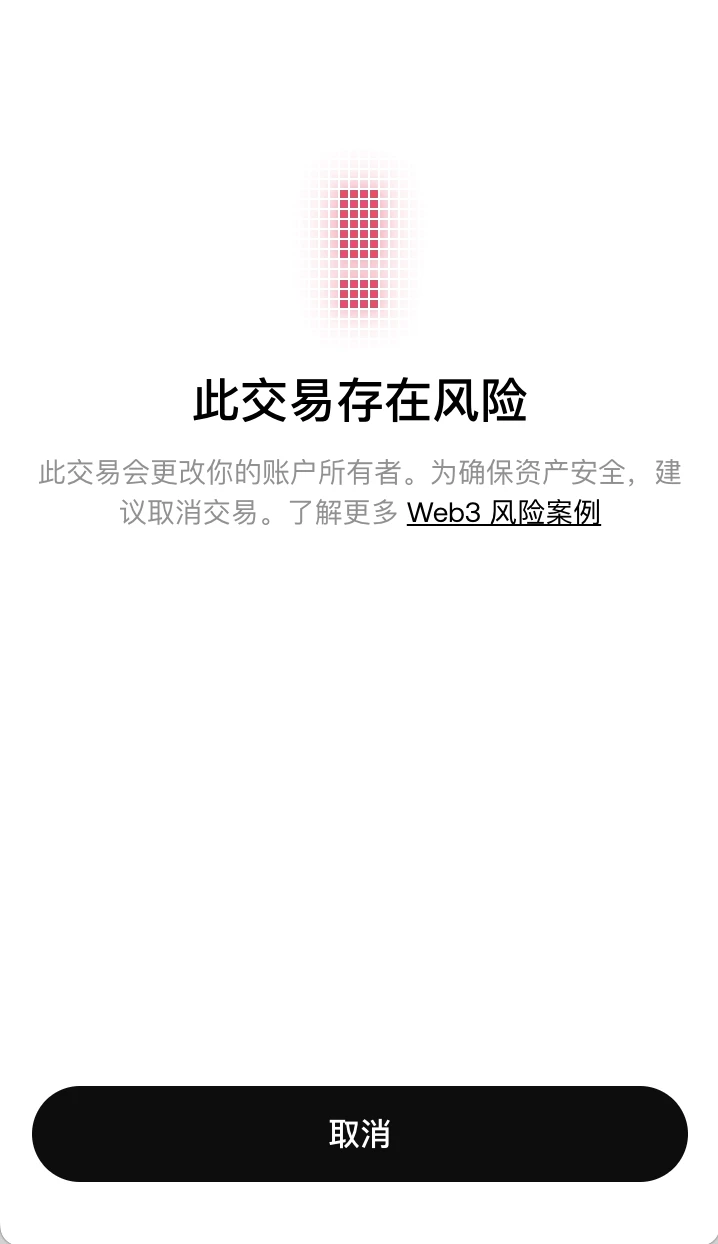
OKX Web3 monitors Solana account owner change risks
In addition to the common authorization risk interception mentioned above, the OKX Web3 wallet also provides security protection for other potential risk scenarios. For example, when Calldata is changed to change the transfer operation to authorization or Permit signature authorization for non-whitelisted DApps, the wallet will issue a security warning in time to remind us to pay attention to the potential risks in the operation and ensure that each step of authorization is within a safe and controllable range.
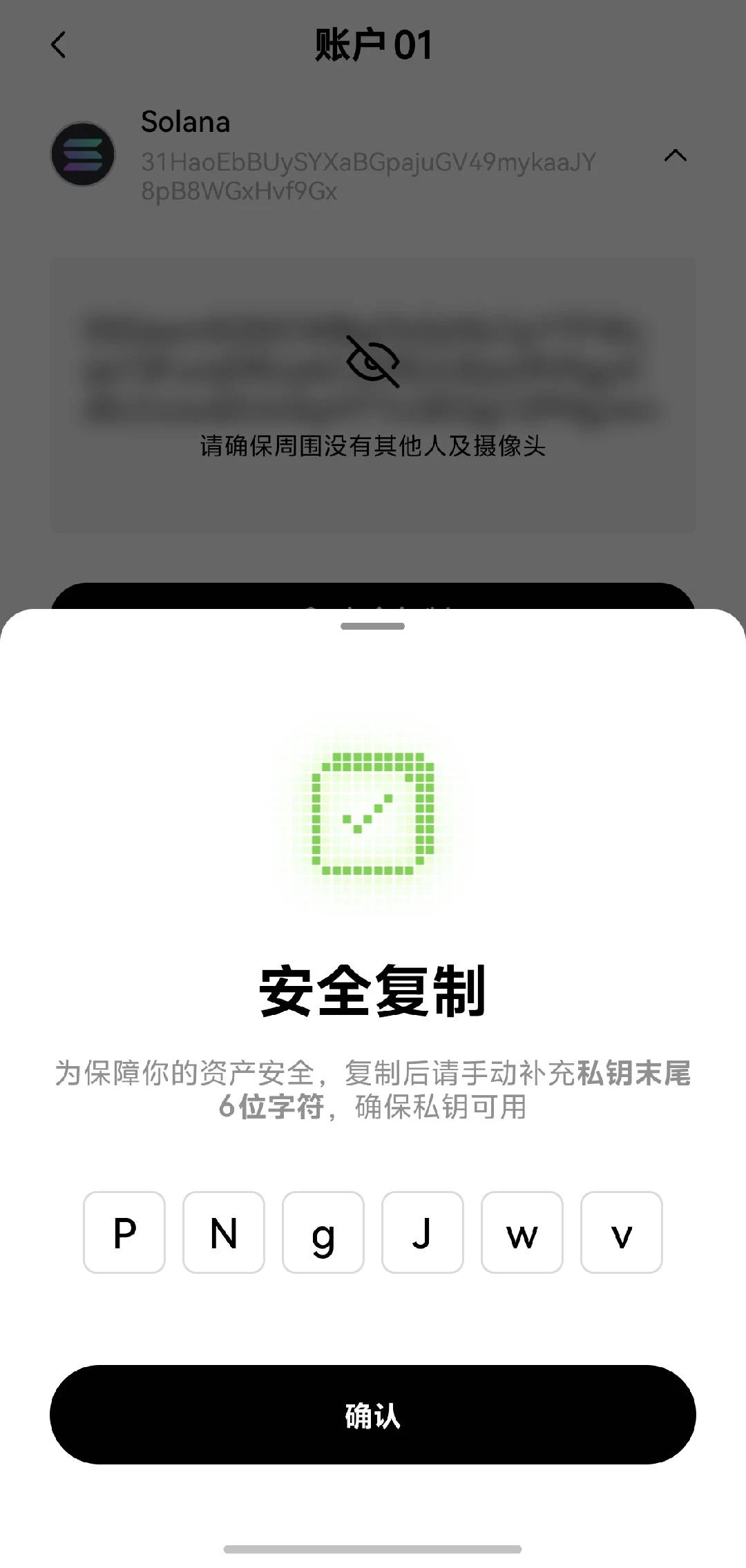
3. Private Key Protection
In addition to malicious token detection and DApp authorization detection, the OKX Web3 wallet has carefully designed protective functions for private key and mnemonic backup and export. Everyone must remember that safety comes first! Especially private key protection, because most of the thefts are caused by private key and mnemonic leakage. The OKX Web3 wallet has implemented ultra-high standard protection, and even screenshots and recordings of private keys and mnemonics are not allowed, completely avoiding the risk of information leakage. In addition, it also supports segmented replication of private keys to ensure that each link is safer, and hackers have no chance at all. At present, only the OKX Web3 wallet supports this function. These measures are like putting a security door on our wallets.
4. MEV Sandwich Attack Prevention
Sandwich attacks are a common arbitrage behavior on decentralized exchanges (DEXs). Attackers use the visibility of transactions on the blockchain to insert two of their own transactions before and after the users transaction to make a profit. Since transactions on the blockchain are public, attackers can monitor unconfirmed transactions in the memory pool (mempool). First send a transaction to increase the price of the target asset (if the victim is a buy order) or lower the price (if the victim is a sell order). The victims transaction is executed as planned, but because the price has been manipulated by the attacker, he will buy at a higher price (or sell at a lower price). After the victims transaction is completed, the attacker sells the assets he just bought to make a profit. OKX Wallet has access to multiple MEV protectors, and the mainstream MEME ecological network is covered to protect users from sandwich attacks.
5. Choose the right tools for safe transactions
In the crypto world, security incidents are not scary, what is really scary is our momentary misjudgment. Every time I use the OKX Web3 wallet, I always feel that it is always a little faster than me, blocking my recklessness, greed and negligence in advance, helping me avoid unnecessary risks.
After several years of working in the cryptocurrency industry, I finally understood what risk control is: it is not to eliminate all threats, but to make these threats visible, so that we can choose the right tools and improve our safety awareness. The OKX Web3 wallet is like a breathing symbiotic armor - it does not prevent me from touching the flame, but it will repair my skin the moment it is burned. Isnt this balance between danger and safety the coolest survival rule in the crypto world?
Only by gaining security can you gain wealth and freedom.
Disclaimer
This article is for reference only. This article only represents the authors views and does not represent the position of OKX. This article is not intended to provide (i) investment advice or investment recommendations; (ii) an offer or solicitation to buy, sell or hold digital assets; (iii) financial, accounting, legal or tax advice. We do not guarantee the accuracy, completeness or usefulness of such information. Holding digital assets (including stablecoins and NFTs) involves high risks and may fluctuate significantly. You should carefully consider whether trading or holding digital assets is suitable for you based on your financial situation. Please consult your legal/tax/investment professionals for your specific situation. Please be responsible for understanding and complying with local applicable laws and regulations.