Original source: SINOHOPE
Overview of the Bybit theft
On February 21, 2025, a Safe multi-signature wallet of the cryptocurrency exchange Bybit was stolen, and crypto assets worth about $1.5 billion disappeared, becoming the largest theft in the history of cryptocurrencies. In this attack, although there was no problem with the Safe multi-signature wallet contract itself, the use process was still attacked. The multi-signature participants lacked sufficient security awareness and reliable independent verification mechanisms when signing, so the hackers tampered with the signature content and completely deceived multiple (3) signatories. Finally, they obtained control of the multi-signature wallet through malicious transactions and completed the attack.
In addition to Bybit’s attack on Safe multi-signature wallets, there have been several other similar attacks before, including:
On July 18, 2024, the Safe multi-signature wallet of the Indian exchange WazirX was attacked, the logical contract was changed, and approximately US$230 million was stolen.
On October 16, 2024, the multi-signature wallet of the lending protocol Radiant Capital Safe was attacked and approximately US$50 million was stolen.
Since the development of the crypto industry, the security issues caused by smart contracts have received high attention from industry practitioners. However, judging from the hacker theft incidents that have occurred in recent years, wallet security issues are still worrying. The Bybit theft incident and similar incidents in the industry have exposed the huge loopholes in wallet security: in the daily management of funds/authorities, under the seemingly safe multi-signature wallet mechanism, there are still systemic problems in the whole process, and wallet security needs to be given enough attention by the entire industry.
Analysis of hacker attack process
According to the information disclosed in the latest investigation report, the process and key doubts of Bybit’s attack are as follows:
The attacker deployed the malicious contract 0xbDd077f651EBe7f7b3cE16fe5F2b025BE2969516 in advance at UTC 2025-02-19 7:15:23;
A developer computer with system publishing permissions of Safe{Wallet} was hacked. The attacker uploaded and modified a javascript code file in Safes AWS S3 bucket at UTC 2025-02-19 15:29:43. The file contained malicious logic and only targeted Bybits Ethereum Safe wallet and an unknown wallet (presumably used by the attacker for testing and verification), thereby completing the hacking of the Safe{wallet} front-end interface.
On UTC 2025-02-21, during the normal hot and cold fund transfer process of Bybit, all Safe{wallet} users saw and used the Safe{wallet} front-end that was implanted with malicious code. Therefore, the Bybit multi-signature participants saw that the information displayed on the Safe{Wallet} front-end interface was completely normal (but the actual signature content did not match the content displayed on the front-end);
The signer uses a Ledger hardware wallet, but the signing process of the Ledger hardware wallet is blind signing. The signer cannot verify whether the content to be signed in the Ledger is consistent with the information displayed on the Safe{Wallet} front-end interface.
The attacker successfully deceived all the signing participants and obtained sufficient (3) signatures; the malicious transaction was constructed to call a function of the malicious contract in the form of DelegateCall that forged an ERC 20 transfer; the malicious function completed the upgrade of the wallet contract, that is, changing the logic implementation contract to the malicious contract deployed in advance by the attacker.
After the malicious transaction was completed, the attacker re-uploaded the normal script file within 2 minutes and deleted the malicious script file.
After that, the attacker gained full control of the multi-signature wallet and took away crypto assets worth nearly $1.5 billion.
In this process, the remaining doubts include:
What is the release process of Safe{wallet} front-end system?
Why can a single developer change the code files of a front-end system hosted in cloud storage without committing the code to the source code repository?
The weak links exposed by the Bybit theft incident
DeFi system front-end security risks
For all DeFi applications, although in theory anyone can create transactions and interact directly with smart contracts on the chain, in reality this is an impossible task for most users in the real world! Therefore, all DeFi applications inevitably require the front-end system to construct transactions or EIP-712 data to be signed. If the same set of smart contracts is not supported by multiple independent front-end systems, then the front-end system of the DeFi application becomes a major single point of risk.
Operating equipment safety hazards
The direct cause of the Bybit incident was the hacking of a computer device of a developer with system publishing permissions from the Safe{Wallet} project, which highlights the eternal existence of traditional security risks. Since Web3 practitioners may be directly involved in the security of funds on the chain, they should be given the highest level of attention in preventing traditional network security risks. All technical systems and management links in the Web3 field should be considered and implemented with reference to financial-level security levels.
Safe Multi-Signature Contract Security Weakness
The Safe multi-signature contract only provides one execution entry: execTransaction, which provides two execution methods: Call and DelegateCall. For batch transactions, the Safe contract itself does not directly open the batch execution entry, but implements the logic of batch transactions using other contracts, such as the MultiSendCallOnly contract. Therefore, when a batch contract needs to be constructed, it is necessary to construct a call transaction to the DelegateCall of the external contract to execute the transaction splitting and one-by-one execution logic of the external contract.
In normal business scenarios, the DelegateCall method should only be executed when the target address (to address) of the interaction is a MultiSendCallOnly contract.
However, this mechanism of Safe leaves potential safety risks for the daily use of Safe. Most users may lack sufficient knowledge, skills and awareness to conduct independent and complete verification during use.
In fact, the three known attacks on Safe Wallet involving huge amounts of money all exploited this mechanism. The attackers successfully used the DelegateCall execution method to make the Safe Wallet execute malicious logic.
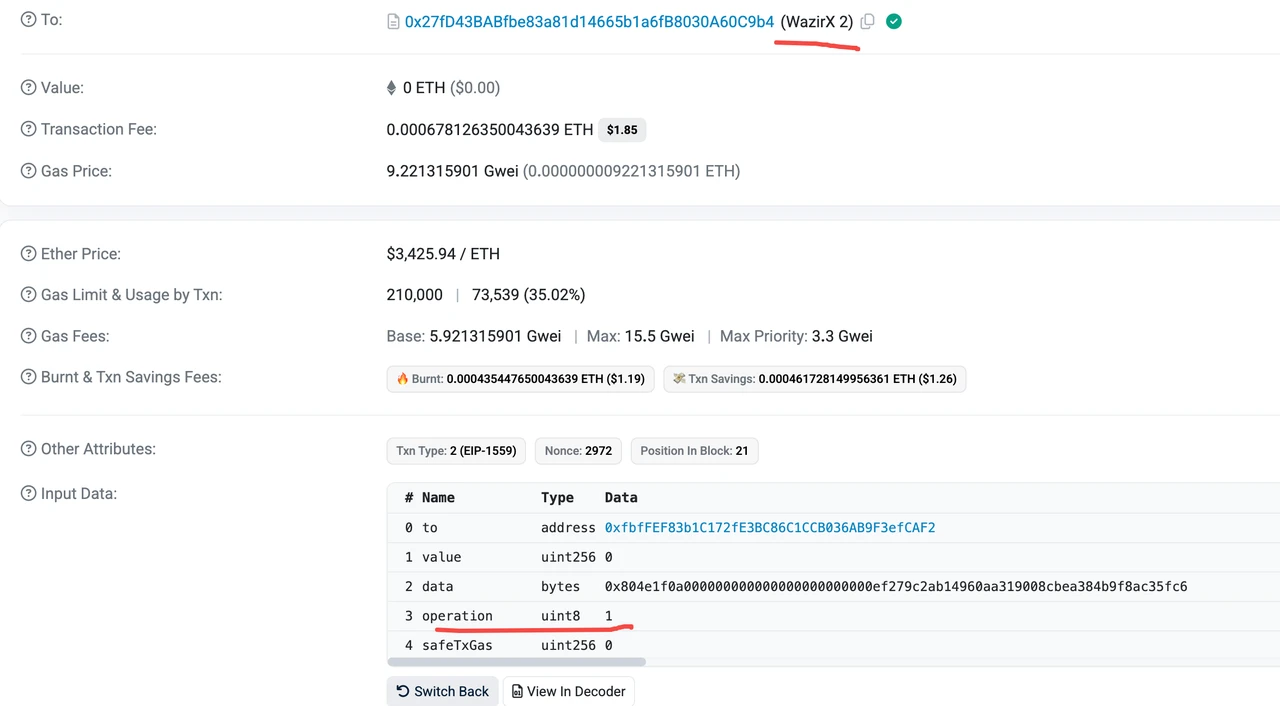
WazirX:
https://etherscan.io/tx/0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d
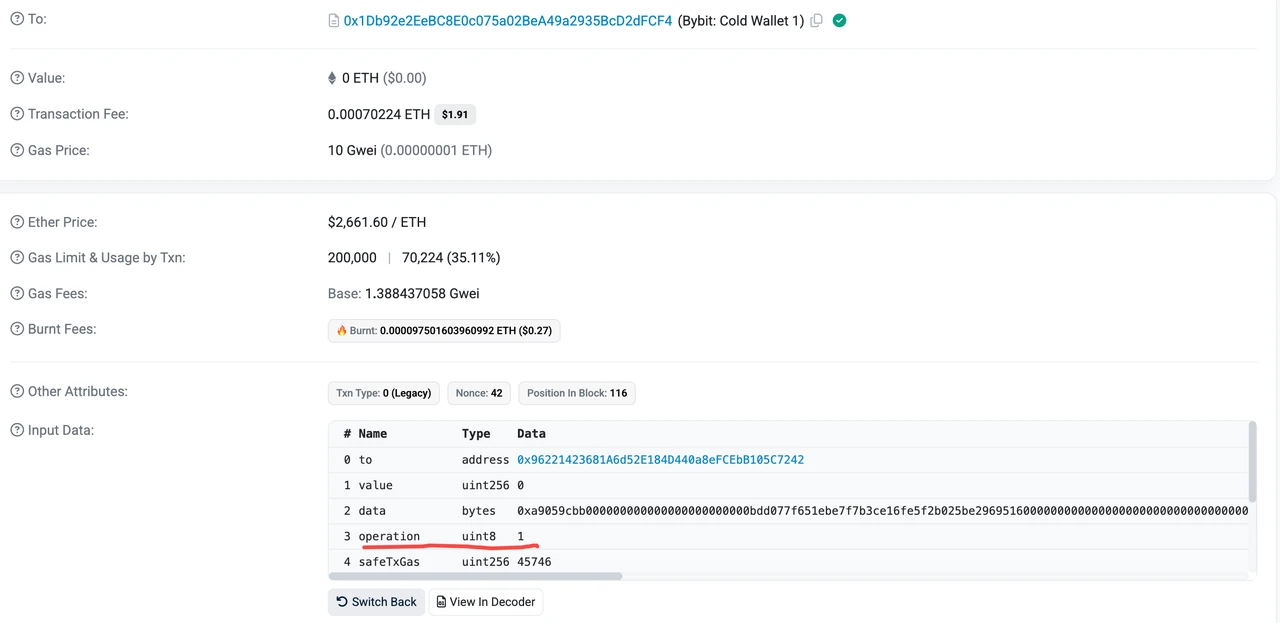
Bybit:
https://etherscan.io/tx/0x46deef0f52e3a983b67abf4714448a41dd7ffd6d32d32da69d62081c68ad7882
Some hardware wallets have the risk of blind signing
The ability of a wallet application to decode signed transaction data is a very important capability. Some wallets that focus on Web3 on-chain interactions already have certain transaction parsing capabilities and are constantly improving them. However, hardware wallets (such as the Ledger hardware wallet used by Bybit in this incident) currently lack such capabilities. People can only sign blindly, losing the last chance to verify the transaction content.
The transaction parsing capability of the wallet requires a large amount of timely updated data support (such as the ABI database in the EVM compatible chain field), as well as the need to identify common specific transaction types and perform certain customized processing. This places high demands on the continuous update and iteration of the wallet.
The awareness of independent verification among multi-signature participants needs to be strengthened
In order to avoid the single-point risk and private key leakage risk of single-signature, the industry has generally turned to the use of multi-signature wallets. However, if the multi-signature participants lack the awareness, ability and necessary tools for independent verification during use, and mainly rely on the security and reliability of the transaction initiator, then the multi-signature wallet will lose its intended function.
Security Practices of SINOHOPE
Crypto Funds Security Principles
For the security of Crypto funds, it is necessary to form a comprehensive and three-dimensional mechanism in terms of security awareness, security technology system, security specifications, etc. In response to the Bybit incident and similar incidents, SINOHOPE specifically emphasized that users need to enhance some basic security awareness.
1. Traditional security reinforcement suggestions
Web3 organizations and personnel should be aware of financial-grade security and take practical measures to prevent traditional security risks.
Enable dedicated devices:
Equip dedicated independent equipment for important purposes, avoid mixing with daily office equipment, and do not activate it unless necessary.
Use a more secure operating system, such as Linux or the latest version of macOS/Windows, and remove unnecessary services and ports.
Strengthen the security of office network equipment and implement traditional security measures:
Terminal/office environment security is still the top priority for protecting against APT attack organizations such as Lazurus. Please ensure that EDR tools are installed on the terminal (traditional antivirus software has limited effect in dealing with APT);
Strengthen access control and protection depth of internal systems. Access to sensitive internal systems and important operations must undergo additional secondary authentication, such as internal code base management and cloud platform management.
Do a good job of permission management for cloud service providers such as CDN/AWS. When logging into the console, please ensure that the scope of personnel, permissions, and access time are minimized. By default, root accounts and admin permission accounts are not used. Use IAM role first and avoid using ak/sk access methods. If it must be enabled, please enable key rotation and add access address whitelists;
Perform integrity checks on publicly accessible resources, such as public SDKs, client installation packages, and static resources cached by CDNs (CloudFront-S 3/CloudFlare-R 2, etc.), and simulate user scenarios for regular checks.
Perform additional integrity checks on each code release to ensure that the online environment code is consistent with the internal security-reviewed code;
Strengthen monitoring of access to internal/supplier systems, promptly detect access from other locations or at abnormal times, and promptly investigate and confirm;
Ensure full coverage of terminal device security capabilities for key authorized personnel.
(II) Basic principles of wallet use
Isolation Principle
Hot and cold isolation
Purpose isolation: Funding wallets are strictly isolated from permission wallets. Funding wallets should only hold funds and have only transfer functions. It is strongly recommended to use a dedicated funding wallet solution instead of using multi-signature contracts such as Safe as a simple funding wallet; multi-signature contract wallets are only considered when the wallet needs to be used as the management authority of on-chain contracts and participate in DeFi applications.
Equipment isolation: Asset-critical equipment, isolated equipment, do not use daily computers/work computers, and do not enable them unless necessary
Avoid single point risk and conduct independent verification by multiple parties
Independent risk control system
Whitelist control
Independent risk control review
Trading simulation execution
The principle of sufficient capabilities and the principle of minimizing authority: reduce risk exposure as much as possible
Cold wallet solution recommendations
1. Enterprise-level fund management solution based on MPC technology
For wallets that only need to manage funds, using a smart contract multi-signature wallet solution that has the potential risk of executing arbitrary logic may not be the best choice.
For cold wallets that only have fund management needs (no need to participate in DeFi interactions), you can use the SINOHOPE enterprise-level MPC wallet solution of Xinhuo Technology, that is, the SINOHOPE self-custody platform as a substitute for Safe multi-signature. For institutional clients with specific needs, SINOHOPE can also provide technical solutions to support customers in realizing the private deployment of MPC solutions.
MPC-TSS (Muti-Party Computation-Threshold Signature Scheme) technology supports distributed management of private key sharding and collaborative signatures, solves the single point risk of private keys, and realizes secure self-custody.
Compared with the multi-signature smart contract solution that is only available on EVM-compatible chains, the MPC-based solution has all the advantages of the Safe multi-signature solution, and also has some advantages that Safe multi-signature does not have, such as multi-chain versatility, better independent auditing, and eliminating the potential risk of executing arbitrary logic. The characteristics of the SINOHOPE MPC solution are summarized as follows:
More autonomous than centralized hosting
Independent control of assets, no fear of misappropriation or running away
Support TN multi-signature to avoid single point risk
Support enterprise multi-level asset management
More secure and more functional than decentralized wallets
Multi-party management of private key sharding eliminates the risks of traditional private key custody
No need to keep an invisible private key or mnemonic phrase
Multi-level disaster recovery solutions and multi-scenario shard recovery mechanisms
More convenient and easier to use than hardware wallets
Sharding can be connected to the Internet, 0 storage difficulty
Web2 product form, quickly master
Cheaper and more versatile than contract wallets
No gas consumption for address creation, low handling fee
Supports most mainstream blockchains
Chain multi-signature to protect privacy
For simple fund management needs, it can better implement business review and risk control, and eliminate the potential risk of executing arbitrary logic.
This can be coupled with the enhanced measure of using a dedicated mobile device, which is only online when reviewing transactions, to further strengthen security.
MPC-TSS technical capabilities and advantages, combined with the online account system, multi-factor authentication system, and biometric technology accumulated over the years on the Internet, can effectively help users eliminate private key mnemonics, prevent theft, loss, and malicious behavior, and ensure user control over their assets.
2. SINOHOPEs signature verification solution for Safe{wallet} multi-signature
In the Web3 field, in addition to simple fund management needs such as cold wallets, there are also needs for on-chain permission management and participation in DeFi interactions. For such needs, the on-chain multi-signature solution represented by Safe{wallet} is undoubtedly still one of the best solutions at present. However, the Bybit incident also exposed multiple weak links in the use of Safe{Wallet} multi-signature, among which the single reliance on the front-end system and the hidden dangers of blind signing in hardware wallets are particularly prominent.
In response to potential risks in the use of Safe{wallet}, SINOHOPE has launched a signature verification solution for Safe{Wallet} multi-signature. By introducing an independent signature content verification mechanism, combined with enterprise-level approval processes and risk control mechanisms, it makes up for the security shortcomings of the hardware wallet + Safe{Wallet} multi-signature solution.
The independent verification scheme of SINOHOPE MPC wallet includes:
For signature requests of Safe{Wallet}, an independent risk control verification strategy is enabled; based on the industry ABI database and targeted processing of Safe contracts, the content to be signed and its execution intention are independently parsed, and early warnings can be issued for risky operations (such as unexpected DelegateCall calls) in a timely manner.
Integrated transaction simulation execution capabilities can simulate transaction execution before signing, identify operation intentions, and display operation intentions and potential risks in a user-friendly manner to avoid blind signing risks.
It can integrate enterprise-level approval processes and formulate special approval processes and risk control strategies for multi-signature wallets managed by MPC wallet accounts to meet more flexible and rich fund management needs.
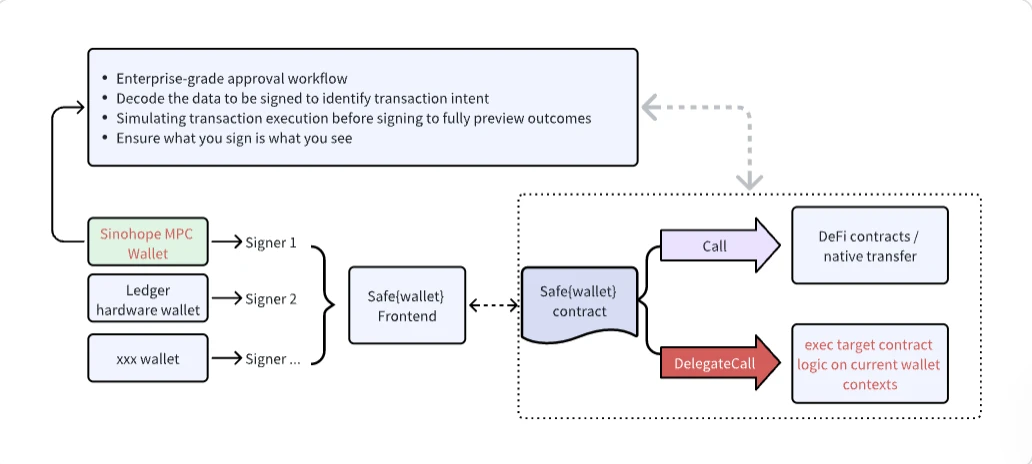
By using the Xinhuo Technology SINOHOPE MPC wallet as a partial Signer member of Safe{Wallet}, an independent security enhancement layer can be introduced into the current Safe{Wallet} multi-signature wallet application system, which is a beneficial supplement to the existing usage scheme. Since the SINOHOPE MPC wallet itself is a self-custodial wallet and only a single signature authority can be held by the SINOHOPE MPC wallet, the customer still always maintains the ultimate control over the Safe wallet/assets.
The signature verification service of SINOHOPE MPC wallet can greatly improve the security of customers in the process of using Safe{Wallet}, and effectively reduce the independent verification skill requirements for users, and reduce the independent verification burden of users, which is more conducive to institutional customers to more closely integrate corporate needs and more reasonably allocate the roles of multi-signature participants (boss, business, finance, security, etc.) while ensuring that each participant has the conditions to implement independent audit and verification, truly realizing the purpose of Safe{Wallet} preventing single point risks and realizing multi-party verification.
Conclusion: Web3 Industry Wallet Security Initiative
Promote industry-wide unified security standards and build a Web3 trusted ecosystem
As the Web3 ecosystem develops rapidly, the security of wallets, as the core and entry point for user asset management, is of vital importance. However, the current security standards in the industry are not unified, resulting in users facing different security risks when using different wallets.
SINOHOPE Initiative:
Establish common industry security standards - build an industry security forum, jointly build best security practice specifications covering all aspects of industry research and development, daily management, user use, etc., build ecological application/security component interoperability standards, and jointly ensure the long-term security of the industry.
Improve user safety awareness - Through standardized safety education, improve industry users risk awareness and prevention capabilities.
Strengthen cross-ecosystem collaboration - Promote information sharing and emergency response mechanisms among industries to jointly respond to security threats.
Security is the cornerstone for the stable and long-term development of the crypto industry. We call on developers, wallet service providers, auditing agencies and the community to work together to promote security standardization and create a safer trading environment for users!










